EMULATING NETGEAR ROUTER FIRMWARE
- Layout for this exercise:

- The goal of this exercise is to emulate firmware corresponding to a Netgear router, both accessing the file system of the firmware and also running it as if it were real.
- Once the emulation is successful the firmware will work as an actual physical device running on the network.
- The reason of emulation is the need to run firmware binaries of embedded devices in a Linux system (x86 architecture), whereas they are intended to work with different architectures like MIPS or ARM.
- In this way, we can analyze and understand the firmware's functionality, or even interact with it for security purposes.
1 - Downloading, extracting and decompressing the firmware
- The Netgear Download Center provides all the firmware for the Netgear devices:
http://downloadcenter.netgear.com/
- For instance, let's download WNAP320 Firmware Version 2.0.3:
- Renaming the file to a more manageable name:
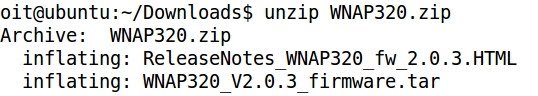
- Extracting and decompressing with unzip and tar:
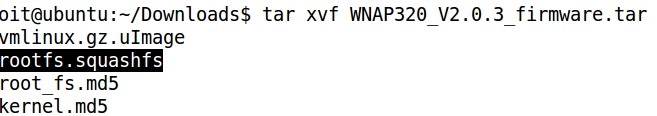
2- Extracting and decompressing the file system of the firmware
- The .squashfs file contains the compressed file system of the firmware:
https://en.wikipedia.org/wiki/SquashFS
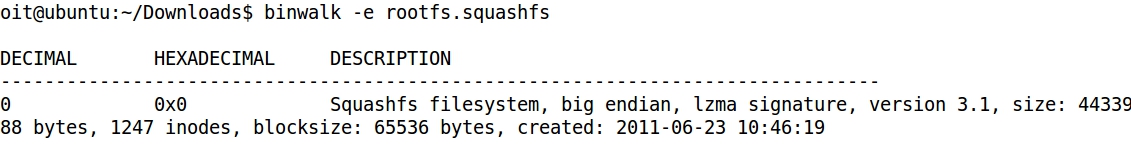
- binwalk -e (extraction) extracts the directory _rootfs.squashfs.extracted:

- The folder squashfs-root contains the decompressed file system of the firmware:
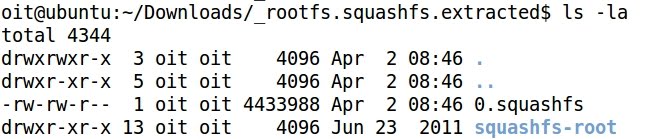
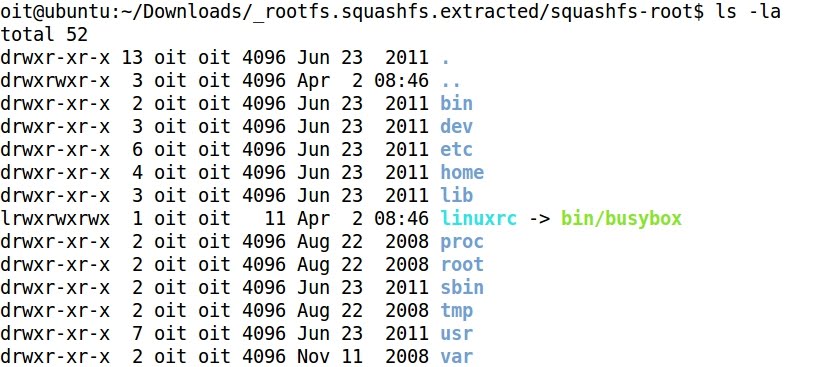
- It is very usual that embedded devices commands are run through busybox, and not directly by /bin/sh or /bin/bash, as it happens with typical Linux systems:
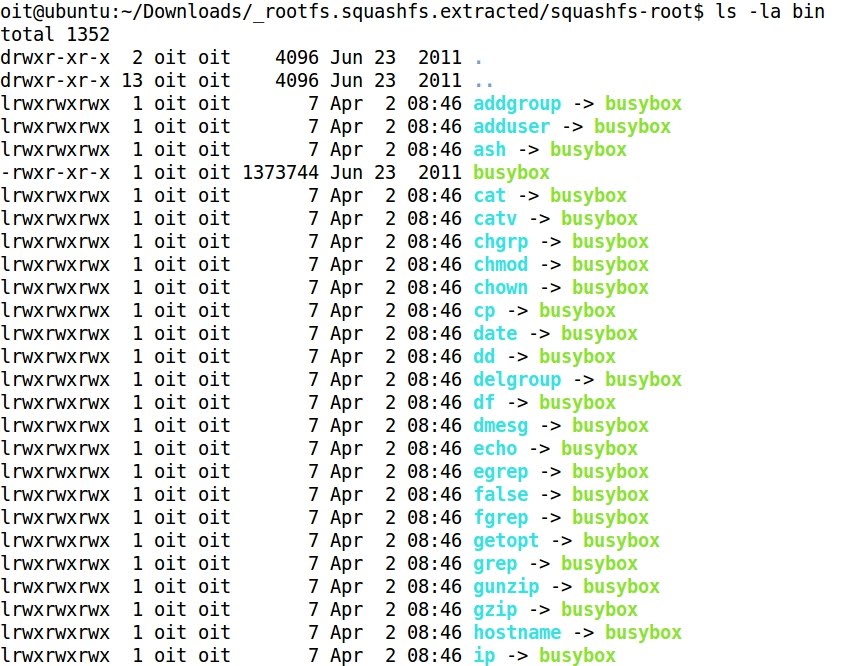
- For more information about busybox:
https://busybox.net/
https://en.wikipedia.org/wiki/BusyBox
3 - Identifying the architecture
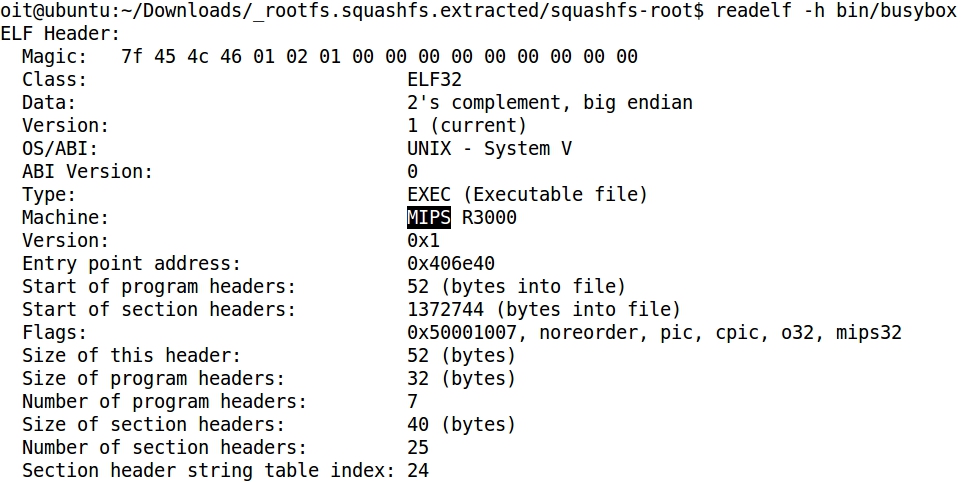
- file command shows that the extracted binaries are intended for the MIPS architecture, and not for the x86 architecture where Linux is running:

- Same result with the comand readelf:
4 - Emulating with FAT (Firmware Analysis Toolkit)
- FAT (Firmware Analysis Toolkit) is composed by a set of tools (qemu, binwalk, mitmproxy, ...) useful to emulate embedded devices firmware.
- It is an open source tool what can be downloaded and configured according to these directions:
https://github.com/attify/firmware-analysis-toolkit
- Copying the downloaded .zip file from the original folder /Downloads to the folder /tools/fat, where FAT is located:
- Launching fat.py the user is prompted to a couple of questions, like the absolute path for the file WNAP320.zip, and the name of the manufacturer, in this case Netgear. That information is stored in a postgres database for the purpose of later utilization.
- Also, two passwords are required to complete the process:
a) password for user firmadyne: firmadyne
b) password for oit: password@123
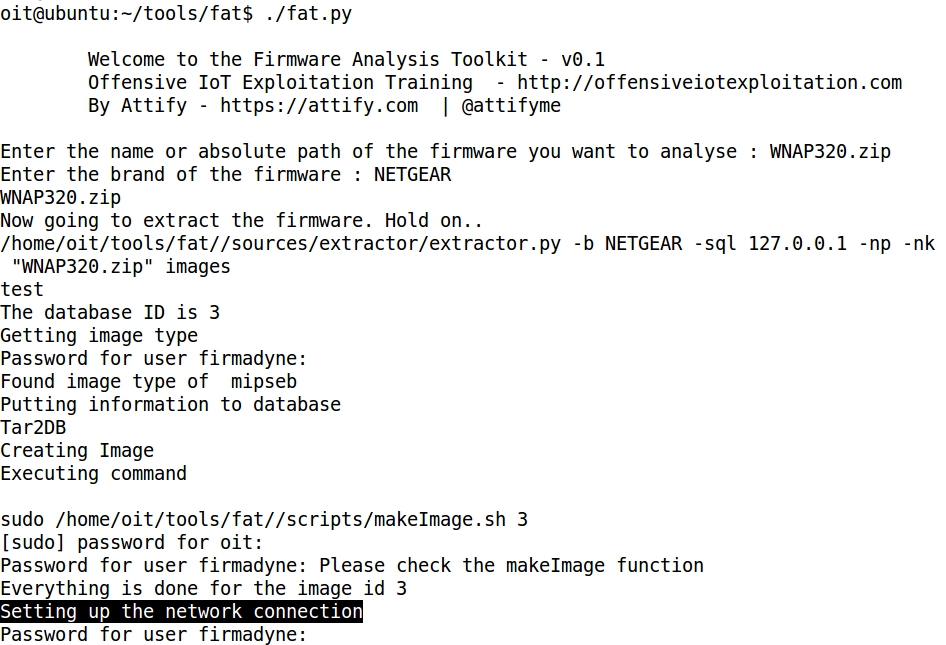
- At this point the network connection is being set up and an interval of 60 seconds must be waited, because that is the time considered to allow the firmware image to boot up.
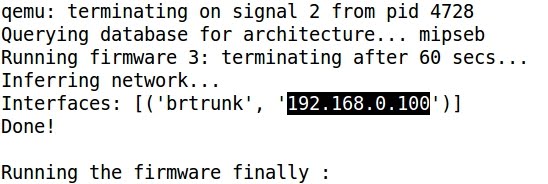
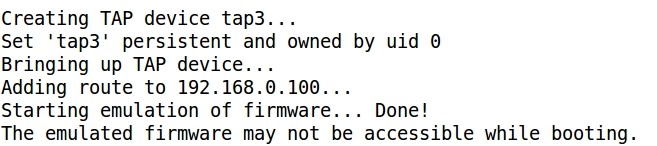
- Finally an IP address is assigned to the virtual interface and the emulated firmware is accessible:
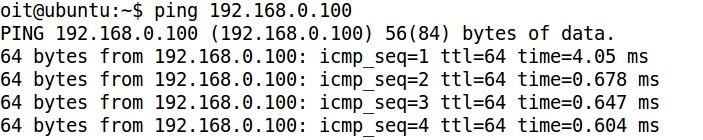
- Pinging the assigned IP address:
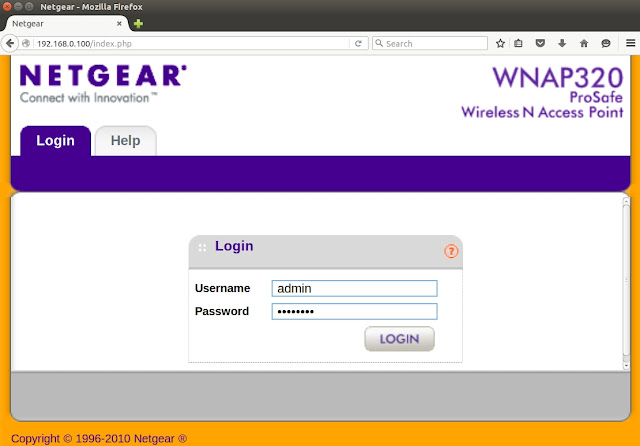
- From the browser the firmware is accessible, after booting, just entering the assigned IP address. The default credentials for this Netgear device are admin:password:
- Once the browser is closed the emulation session is destroyed: