REVERSING AND CRACKING AN ANDROID APPLICATION
1 - Connecting with ADB
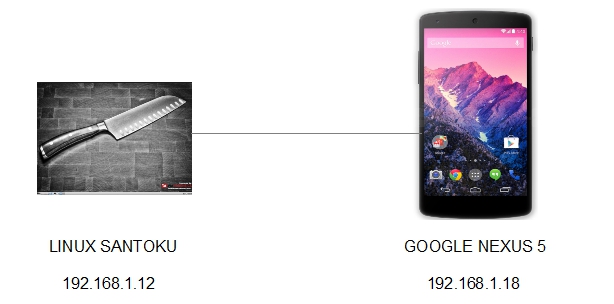
- Linux Santoku connects to Google Nexus 5 (4.4.4 API 19) using Android Debugger Bridge (ADB):
2 - Installing the application
- cocon.apk is an application developed by Anant Shrivastava, and presented for the event Capture The Flag at the conference C0C0N.
- The goal of this exercise is to crack the application for discovering a hidden key.
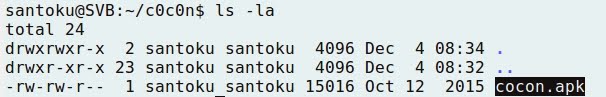
- cocon.apk is available at Santoku machine:
- Installing the application on Nexus 5:
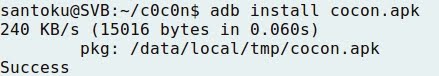
- The application is now installed on the mobile device:
- Launching the application:

- The output tells "Key is disabled". So, that is the key to be discovered along this exercise:

3 - Decompiling the application
- Using apktool with option d the application is decompiled. The output is redirected to the directory Cocon:
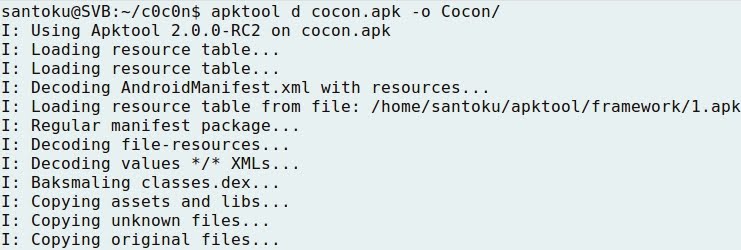
- Checking the contents of the new directory:
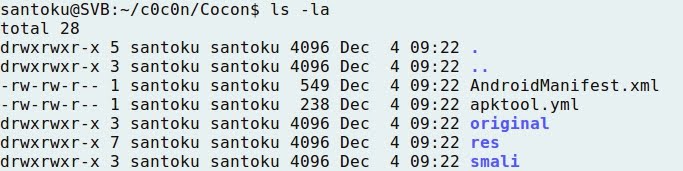
4 - Analyzing the application
- About the manifest of the application:
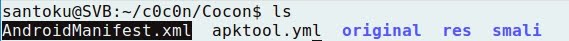
- The package used by the application is called "coc.on":
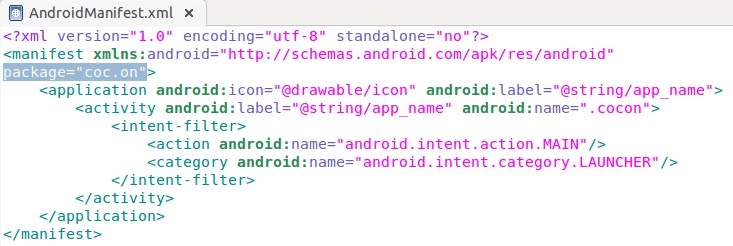
- "coc" and "on" are subdirectories recursively located inside the "smali" directory:
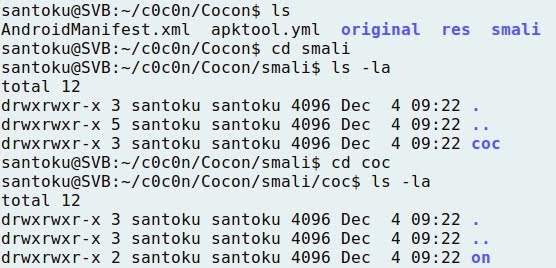
- Reaching "on" directory, the file "cocon.smali" is found:

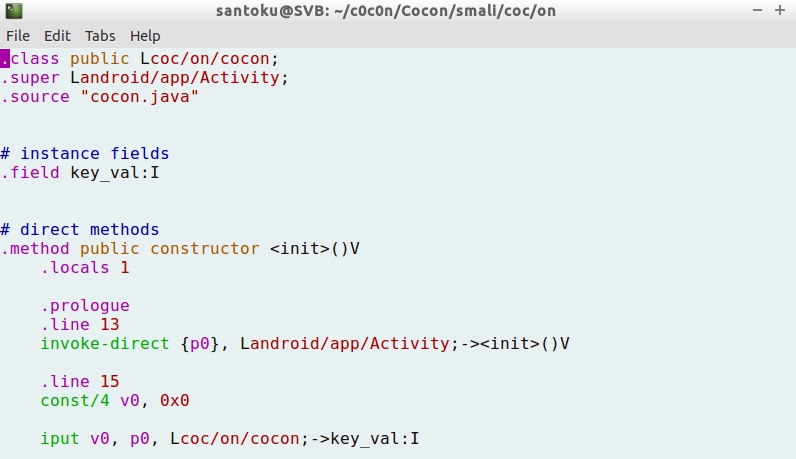
- The smali file contains a representation of the Java code. Not being the actual code, however it is a very good approach to understand how the Java source code is written and how the app works:

etc ...
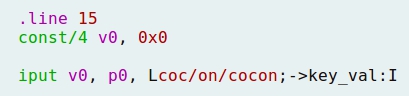
- It is interesting to notice that a constant is created with value 0, and stored into register v0. Also, the value of register v0 is put into register p0, and eventually into the integer key_value:
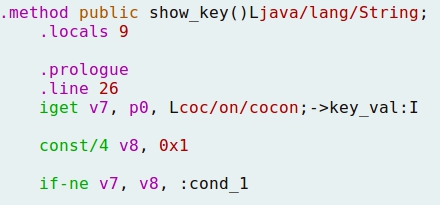
- The "show_key" method creates a constant with value 1, stored into register v8. Also, register v7 gets the value from p0, and finally compares v7 and v8 contents. In case of not matching, it jumps to cond_1:
5 - Cracking and rebuilding the application
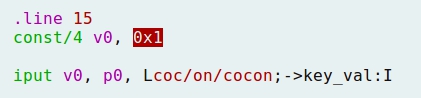
- Now, with the purpose of skipping cond_1, values of v7 and v8 should match, so the value of v0 (later in the program transferred to v7) is changed from 0 to 1:
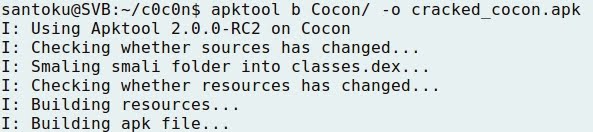
- Once patched the application, it must be recompiled or built again, using apktool with option b. The output will be the new application cracked_cocon.apk:
6 - Signing the cracked application
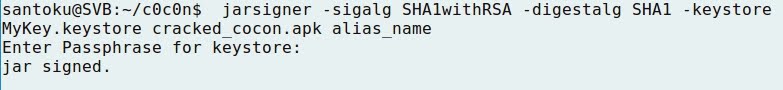
- The new application is signed:
- Verifying that the application is correctly signed:
7 - Installing and testing the cracked application
- Before installing the new application, the old one must be uninstalled:

- Now, cracked_cocon.apk is installed into Nexus 5 with ADB:
- Running the application:

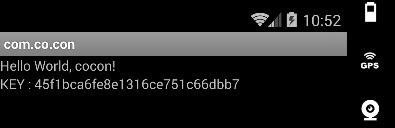
- The cracking process is successful, because now the key is enabled and displayed on the screen of the mobile device: