COMMAND INJECTION WITH BURP FOR NETGAR ROUTER EMULATED FIRMWARE
- Layout for this exercise:

1 - Introduction
- This exercise is based on the Command Injection attack for NetGear devices registered here:
http://firmware.re/vulns/acsa-2015-001.php

- The vulnerability affects a great range of NetGear products, including the router WNAP320:
 - One of the affected scripts is called boardDataWW.php, that will be analyzed for the purpose of attacking it through a Command Injection, sending a crafted input taking advantage of the lack of sanitization:
- One of the affected scripts is called boardDataWW.php, that will be analyzed for the purpose of attacking it through a Command Injection, sending a crafted input taking advantage of the lack of sanitization:

- The vulnerable section of the script uses an insecure call to PHP function exec(), accepting any type of input for the parameter 'macAddress':

2 - Setting up the lab
- Unzipping and decompressing the firmware of the NetGear router:


- Extracting the .squashfs file:

- A new folder is extracted:

- Inside, we can find the whole root file system of the firmware, ready to be analyzed:


3 - Analyzing the vulnerable PHP script
- First, let's try to locate the vulnerable script boardDataWW.php, using the command locate:


- Opening boardDataWW.php we find the call to the PHP function exec():


- The parameter 'macAddress' is passed without further sanitization about the standard MAC address format:

- Let's see how exec() works:

4 - Intercepting with Burp
- Once the firmware emulated is available (as done in previous exercise):

- Going to the affected script:

- Enabling the proxy at the browser:

- Launching Burp:



- Enabling Burp to intercept Client requests and Server responses:

- Sending a fake MAC address:

- The message is intercepted:

5 - Launching the attack
- Sending the request to the Repeater:


- Now, let's try to craft the MAC address input so that the content of /etc/passwd is leaked to a file located into the root of the web page:
cp /etc/passwd /home/www/passwd # from here it is a comment

- Clicking Go and trying to access passwd from the browser:

- The file passwd is open and saved:

- The content of /etc/passwd has been leaked, so the attack is successful:

- Also, because Burp has been enabled to intercept the Server responses, the whole content is displayed:

- It is interesting to notice that this attack has been launched against an "emulated firmware", and not against an actual physical device.
CRACKING AUTHENTICATION WITH BURP FOR NETGEAR ROUTER EMULATED FIRMWARE
- Layout for this exercise:

- This exercise is based in a previous emulation of Netgear firmware:

- Downloading the free edition of Burp Suite in its .JAR file version:
https://portswigger.net/burp/freedownload


- The .JAR file is downloaded:

- Launching the application:

- After accepting all the default options for Burp, let's ensure that the proxy is listening locally (127.0.0.1) on port 8080:

- Also, let's configure Burp so that the interception applies for both the Client requests and the Server responses:

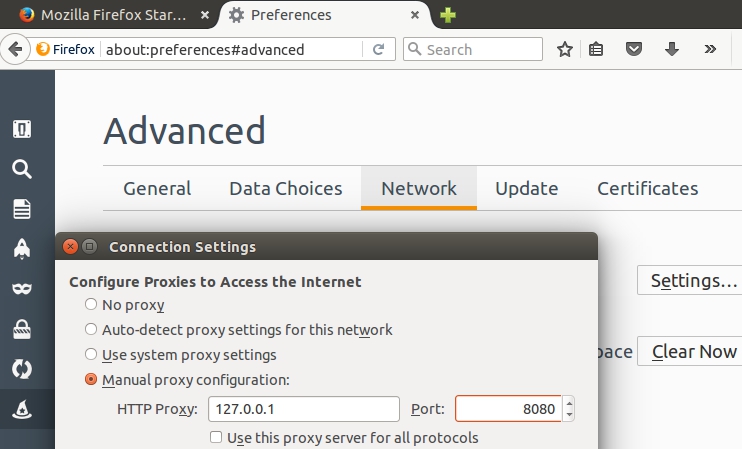
- Now, it is time to enable the proxy at the Firefox browser:
- Let's introduce some fake credentials, like for instance Username:Password

- Burp intercepts and displays the fake credentials:

- Looking into the tab "HTTP history", right clicking the request and choosing the option "Send to Intruder":

- The attack target is the known one (Firmware emulation with 192.168.0.100 and port 80):

- The attack consists on using two payload lists, the first one for the username and the second one for the password:

- Because this is a simple example, let's provide just 10 possible usernames and 10 possible passwords, totally 10x10 = 100 possible requests.
- For the username (list of 10):

- For the passwords (list of 10):

- As said before, in this simple case the total Request count is 100 (10x10):
 - However, in a real scenario case, and using the Pro version of Burpsuite, large wordlist text files could be provided. Of course, trying many possible combinations would take a longer time to perform the attack:
- However, in a real scenario case, and using the Pro version of Burpsuite, large wordlist text files could be provided. Of course, trying many possible combinations would take a longer time to perform the attack:

- Starting the attack:
 - It is noticeable that the only trial (number 3) with a status 200 OK and different length (313) corresponds to admin:password, what are the default credentials for the NetGear device, meaning that the attack is successful.
- It is noticeable that the only trial (number 3) with a status 200 OK and different length (313) corresponds to admin:password, what are the default credentials for the NetGear device, meaning that the attack is successful.
- Also, the 3th trial yields a loginok response message:

- It is interesting to notice that this attack has been launched against an "emulated firmware", and not against an actual physical device.
EMULATING NETGEAR ROUTER FIRMWARE
- Layout for this exercise:

- The goal of this exercise is to emulate firmware corresponding to a Netgear router, both accessing the file system of the firmware and also running it as if it were real.
- Once the emulation is successful the firmware will work as an actual physical device running on the network.
- The reason of emulation is the need to run firmware binaries of embedded devices in a Linux system (x86 architecture), whereas they are intended to work with different architectures like MIPS or ARM.
- In this way, we can analyze and understand the firmware's functionality, or even interact with it for security purposes.
1 - Downloading, extracting and decompressing the firmware
- The Netgear Download Center provides all the firmware for the Netgear devices:
http://downloadcenter.netgear.com/
- For instance, let's download WNAP320 Firmware Version 2.0.3:
- Renaming the file to a more manageable name:
- Extracting and decompressing with unzip and tar:
2- Extracting and decompressing the file system of the firmware
- The .squashfs file contains the compressed file system of the firmware:
https://en.wikipedia.org/wiki/SquashFS
- binwalk -e (extraction) extracts the directory _rootfs.squashfs.extracted:
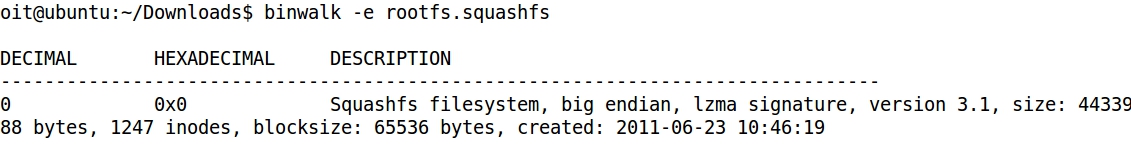
 - The folder squashfs-root contains the decompressed file system of the firmware:
- The folder squashfs-root contains the decompressed file system of the firmware:
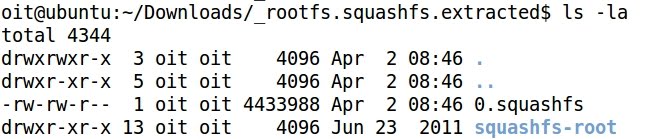
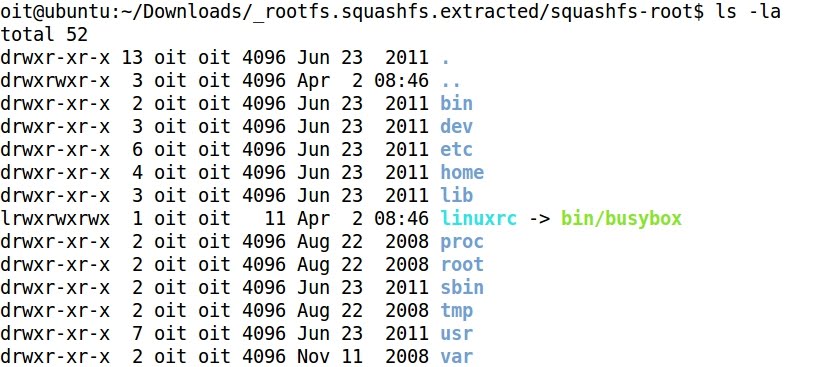
- It is very usual that embedded devices commands are run through busybox, and not directly by /bin/sh or /bin/bash, as it happens with typical Linux systems:
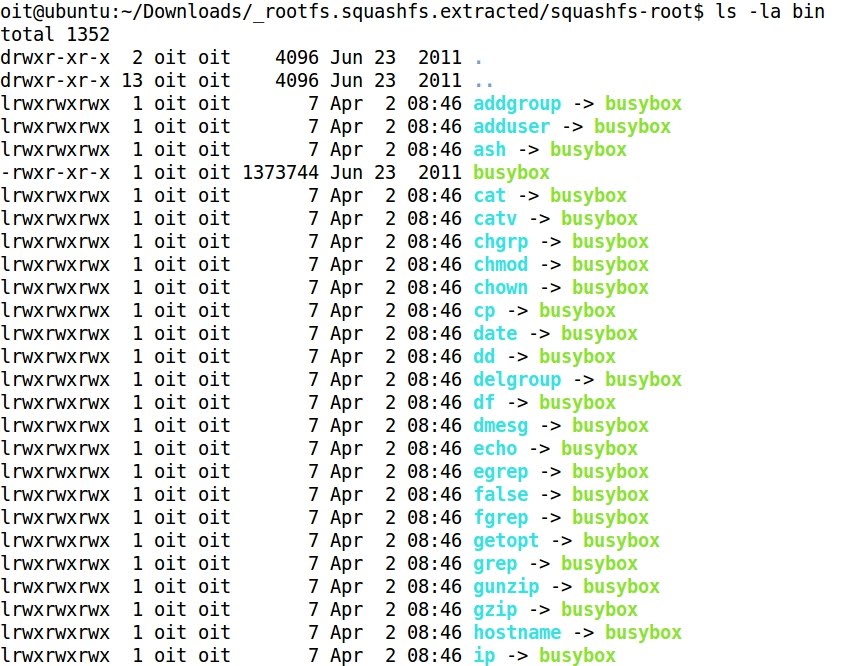
- For more information about busybox:
https://busybox.net/
https://en.wikipedia.org/wiki/BusyBox
3 - Identifying the architecture
- file command shows that the extracted binaries are intended for the MIPS architecture, and not for the x86 architecture where Linux is running:

- Same result with the comand readelf:
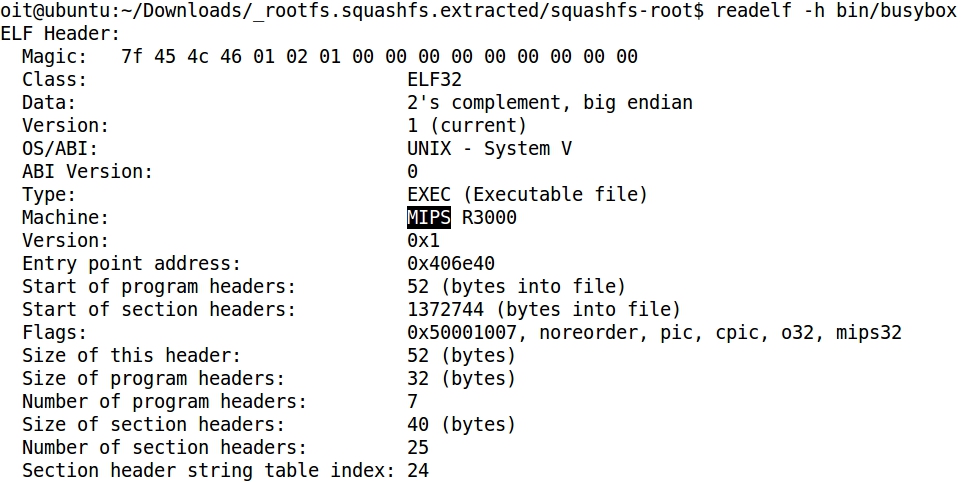
4 - Emulating with FAT (Firmware Analysis Toolkit)
- FAT (Firmware Analysis Toolkit) is composed by a set of tools (qemu, binwalk, mitmproxy, ...) useful to emulate embedded devices firmware.
- It is an open source tool what can be downloaded and configured according to these directions:
https://github.com/attify/firmware-analysis-toolkit
- Copying the downloaded .zip file from the original folder /Downloads to the folder /tools/fat, where FAT is located:
- Launching fat.py the user is prompted to a couple of questions, like the absolute path for the file WNAP320.zip, and the name of the manufacturer, in this case Netgear. That information is stored in a postgres database for the purpose of later utilization.
- Also, two passwords are required to complete the process:
a) password for user firmadyne: firmadyne
b) password for oit: password@123
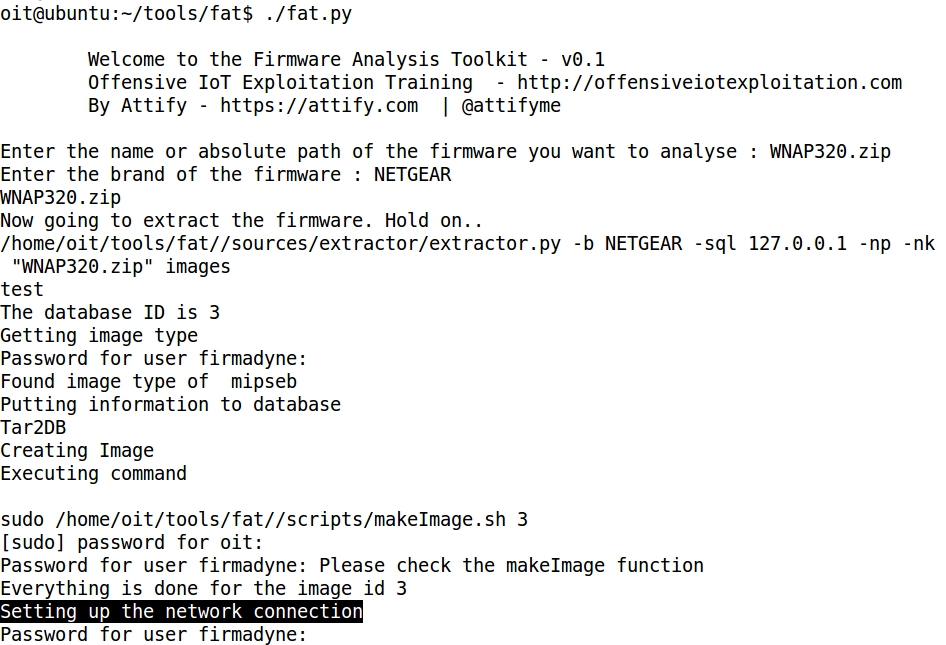
- At this point the network connection is being set up and an interval of 60 seconds must be waited, because that is the time considered to allow the firmware image to boot up.
- Finally an IP address is assigned to the virtual interface and the emulated firmware is accessible:
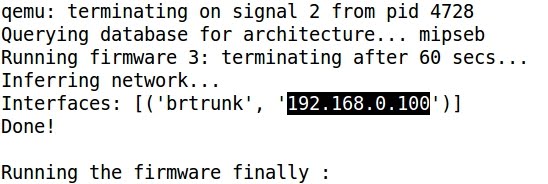
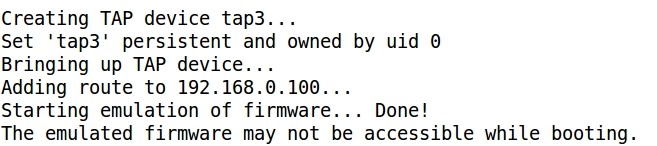
- Pinging the assigned IP address:
- From the browser the firmware is accessible, after booting, just entering the assigned IP address. The default credentials for this Netgear device are admin:password:
- Once the browser is closed the emulation session is destroyed: