SYMFONOS_3
- Layout for this exercise:
1 - INTRODUCTION
- The goal of this exercise is to develop a hacking process for the vulnerable machine Symfonos_3, from the VulnHub pentesting platform.
- Symfonos_3 can be downloaded from here:
https://www.vulnhub.com/entry/symfonos-31,332/
- Once the virtual machine downloaded and extracted with VirtualBox:
2 - ENUMERATION
- Scanning with Nmap:
- Browsing the web server:
- View-sourcing there is a note about "underworld":
- Dirbusting the web server we find /cgi-bin/underworld:
- Going to /cgi-bin/underworld:
- Output is similar to command uptime:
3 - EXPLOITATION
- Metasploit has some exploits related to cgi script, for instance this one related to vulnerability Shellshock:
https://www.rapid7.com/db/modules/exploit/multi/http/apache_mod_cgi_bash_env_exec/
- A Meterpreter session is triggered:
- Getting a shell:
- One interesting thing about user cerberus is that he belongs to group pcap, as previous image shows.
- So the right tools for reading .pcap files are tcpdump and Wireshark.
- First, running tcpdump at local interface and saving to file.pcap:
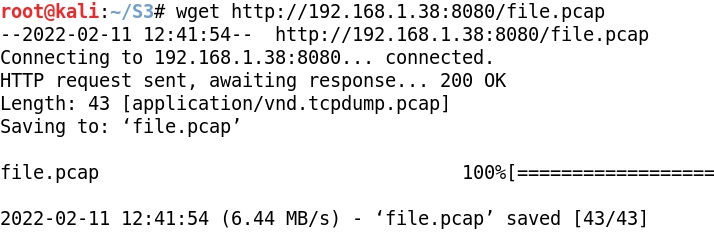
- Now we've got a file.pcap that can be transferred to Kali to be analyzed with Wireshark:
- Opening file.pcap with Wireshark, putting a filter for FTP traffic and following the stream we discover credentials for user hades:
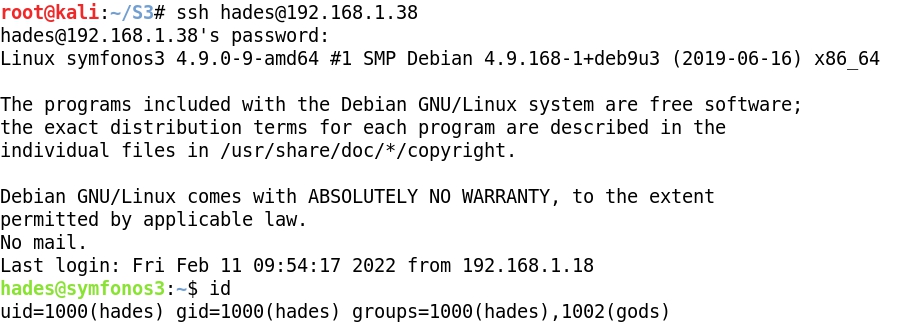
- Now, we can try SSH with these credentials: hades: PTpZTfU4vxgzvRBE
4 - PRIVILEGE ESCALATION
- The new user hades belongs to group gods:
- Let's find files owned by group gods, for instance sitecustomize.py has root privileges:
- sitecustomize.py is a Python script that can be adpated to our needs:
- Just adding these 3 lines at the beginning of the file:
- Setting a Netcat listener:
- Running sitecustomize.py we get a root shell:
5 - CAPTURING THE FLAG
- Reading proof.txt: