CHATTERBOX
- Layout for this exercise:

1 - INTRODUCTION
- The goal for this exercise is to develop a hacking process for the vulnerable machine Chatterbox, what is a retired machine from the Hack The Box pentesting platform:
https://www.hackthebox.eu/
2 - ENUMERATION
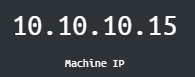
- Chatterbox's IP is 10.10.10.74:

- Scanning with Nmap:

- So threre are just two open ports, both of them running the Achat program.
3 - EXPLOITATION
- Searching for exploits related with Achat there are some of them available, for instance the 36025.py what exploits a Remore Buffer Overflow:



- Copying 36025.py to the local working directory:

- Reading 36025.py we learn s that is designed to execute calc.exe at a Windows machine:

etc ....
- Also, by default it uses this server address IP:

- So what we will do is to replace the shellcode provided at 36025.py by using Msfvenom changing the payload, local host and local port:
- payload -> windows/shell/reverse_tcp
- LHOST = 10.10.14.8 (my machine)
- LPORT = 1234

- Editing 36025.py, copying and pasting here the shellcode originated at previous step with Msfvenom:


- Also, changing the default IP to Chatterbox's IP (10.10.10.74):


- Now, setting a listener session with Metasploit:

- Running 36025.py:

- As a consequence a remote shell is succesfully achieved:

4 - CAPTURING 1st FLAG
- Reading the first flag user.txt is easy:

5 - PRIVILEGE ESCALATION
- However access to the second flag root.txt is denied, so we need Privilege Escalation:

- Remembering that we are running the system as user Alfred:

- There is something weird because user Alfred is the owner of root.txt:

- ICACLS stands for Integrity Control Access Control List, and it displays or modifies discretionary access control lists (DACLs) on specified files, and applies stored DACLs to files in specified directories:
https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/icacls
- icacls.exe grants full access to user Alfred over root.txt:

6 - CAPTURING THE 2nd FLAG
- Now it is possible for user Alfred to read root.txt: