SYSTEM INTEGRITY CHECKING WITH AIDE (ADVANCED INTRUSION DETECTION ENVIRONMENT)
- Layout for this exercise:

1 - Introduction to AIDE
- AIDE (Advanced Intrusion Detection Environment) is an open source host based file and directory integrity checker that was initially developed as a free replacement for Tripwire licensed under the terms of the GNU General Public License (GPL).
- AIDE is used on many Unix-like systems as an inexpensive baseline control and rootkit detection system. This is mainly useful for security purposes, given that any malicious change which could have happened inside of the system would be reported by AIDE.
- AIDE takes a "snapshot" of the state of the system, register hashes, modification times, and other data regarding the files defined by the administrator, building a database that is saved and may be stored on an external device for safekeeping.
- When the administrator wants to run an integrity test he places the previously built database in an accessible place and commands to compare the database against the real status of the system. In case a change has happened to the computer between the snapshot creation and the test, AIDE will detect it and report it to the administrator.
- Also AIDE can be configured to run on a schedule and report changes daily using scheduling technologies such as cron.
https://en.wikipedia.org/wiki/Advanced_Intrusion_Detection_Environment
2 - Installing and configuring AIDE
- Installing AIDE that is available by default in the Ubuntu repository:
- Verifying the AIDE version:
- The configuration file is located into the /etc/aide directory
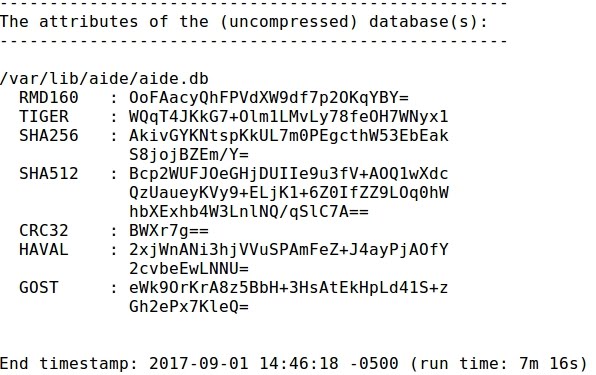
- The database is located inside /var/lib/aide. At this initial moment it is empty:
- Initializing the database with aideinit:
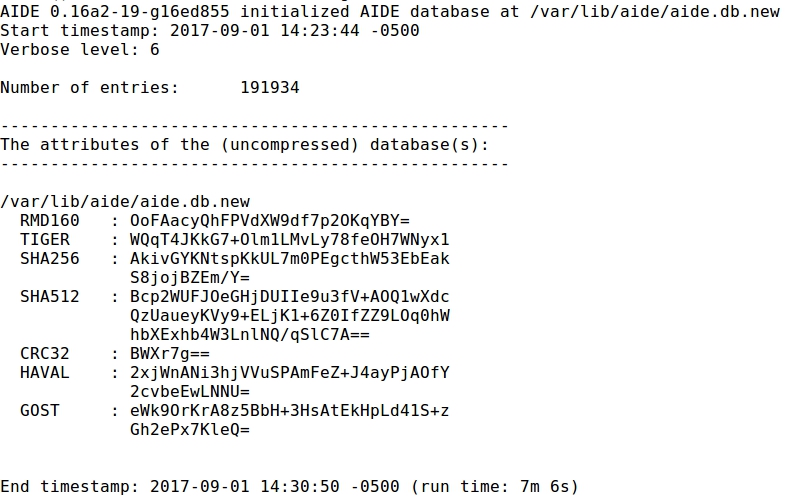
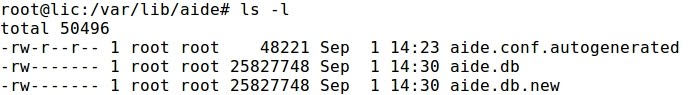
- A new database has been generated that must be installed :
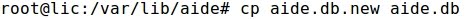
- Building a new AIDE configuration file:
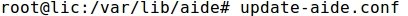
- Copying the new configuration file to the /etc/aide directory:
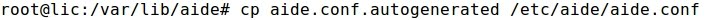
3 - Making some changes to the system
- With the purpose of checking the proper functionality of AIDE let's make some changes to the system.
- For instance creating a new directory and file:
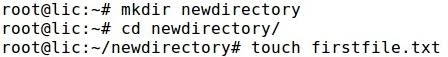
- Also, installing new applications like SSH:

- Starting the SSH daemon:

- By default, the directive for SSH root login is set to "prohibit-password":
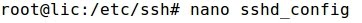
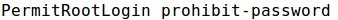
- Modifying sshd_config to set that directive to "yes":
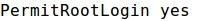
4 - Testing AIDE
- Finally, running AIDE let's see if those changes to the system are detected:
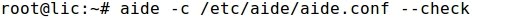
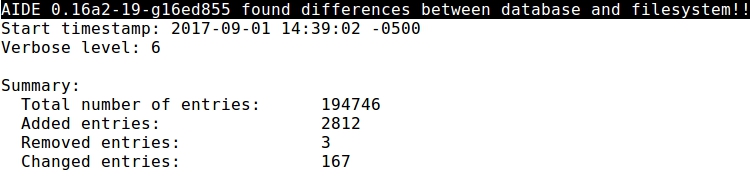
- Because the output is huge let's just focus on some of the most noticeable lines provided by AIDE.
- There are some entries related to installing SSH service and changing configuration:
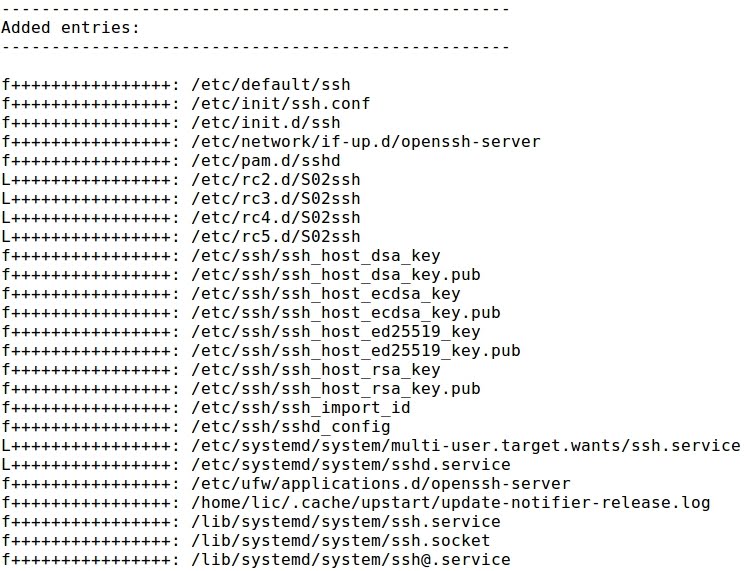
- Entries related with starting the SSH service:
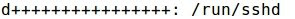
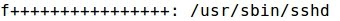
- Also, there are entries related with the newly created directory and file:

- The AIDE checking ends up with information about the new database, timestamping that it has been run for 7m 16s: