SSH TUNNELING (III): DYNAMIC PORT FORWARDING WITH PROXYCHAINS
- Layout for this exercise:

1 - Introduction
- Port forwarding via SSH (SSH tunneling) creates a secure connection between a local computer and a remote machine through which services can be relayed.
- Dynamic port forwarding connections are forwarded via the SSH client, then via the SSH server, and finally to several destination servers
- Dynamic port forwarding turns the SSH client into a SOCKS proxy server.
- SOCKS is a protocol for programs to request any Internet connection through a proxy server.
- The -D 8080 option specifies dynamic port forwarding with 8080 as the SOCKS port.
- One of the most common uses for SOCKS is circumvention, allowing traffic to bypass internet filtering to access content that is otherwise blocked.
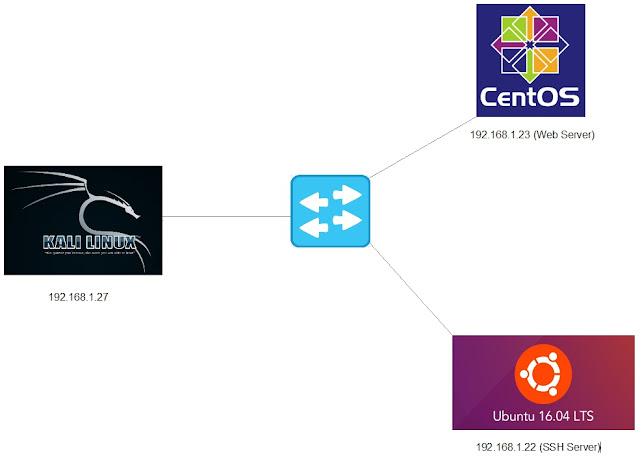
- In our scenario we will use SOCKS to create a dedicated tunnel between Kali and the Windows Server 2008.
- Proxychains allows to interface with the SOCKS tunnel, piping all data that an application would normally just push out to the network through normal means, through proxychains into the SOCKS tunnel up to Windows Server 2008's internal interface.
https://en.wikipedia.org/wiki/Tunneling_protocol
https://en.wikipedia.org/wiki/SOCKS
http://proxychains.sourceforge.net/howto.html
2 - SSH Dynamic Port Forwarding
- In this scenario we assume that the intermediate Windows Server 2008 (two inferaces: 192.168.1.24 and 10.10.10.1) has been exploited by the attacker Kali Linux (192.168.1.27).
- As part of the post exploitation step we will use the Windows Server 2008 machine as a proxy to attack the internal LAN (10.10.10.0/24), for instance the Windows 7 (10.10.10.2) machine.
- SSH -D (Dynamic) option allows to bind the local port 808:

- Running ssh with -D option against the exploited (so we know some credentials) Windows Server 2008:

- Runnig ipconfig we learn that Windows Server 2008 has got two Ethernet IP addresses, meaning that it is connected to outside trough 192.168.1.24 and to the internal LAN through 10.10.10.1:

3 - Proxychains
- Opening a new Terminal different than the one used for the SSH connection:

- Proxychains allows to perform a port scanning inside the internal LAN 10.10.10.0/24. To simplify, let's scan just the port 3389 (RDP-Remote Desktop Protocol) at the first 10 hosts:

- We have discovered that there is an internal host 10.10.10.2 that is running RDP service on port 3389.
- Now, using proxychains again let's run the rdesktop command for the internal host 10.10.10.2:

- The attack is eventually successful:

4 - Checking the ESTABLISHED connections
- It is interesting to check how each one of the hosts implied "sees" the connections.
- Kali Linux works on the SSH Dynamic SOCKS port 8080, and also it is connected to the port 22 of the Windows 2008 that acts as an SSH server:

- The Windows Server 2008 sees two connections, on the one side the mentioned one with Kali Linux, and on the other side a connection with Windows 7 at port 3389 (RDP):

- Finally, Windows 7 is only aware of its connection with Windows Server 2008, although it is actually Kali (the attacker) who is enjoying the Remote Desktop Connection session:

SSH TUNNELING (I): LOCAL PORT FORWARDING
- Layout for this exercise:
1 - Introduction
- A Secure Shell (SSH) tunnel consists of an encrypted tunnel created through an SSH protocol connection.
- Users may set up SSH tunnels to transfer unencrypted traffic over a network through an encrypted channel.
- To set up a local SSH tunnel, one configures an SSH client to forward a specified local port to a port on the remote machine.
- Once the SSH tunnel has been established, the user can connect to the specified local port to access the network service. The local port does not have to be the same as the remote port.
- SSH tunnels provide a means to bypass firewalls that prohibit certain Internet services so long as a site allows outgoing connections.
https://en.wikipedia.org/wiki/Tunneling_protocol#Secure_Shell_tunneling
- In this exercise we are using 3 Linux machines:
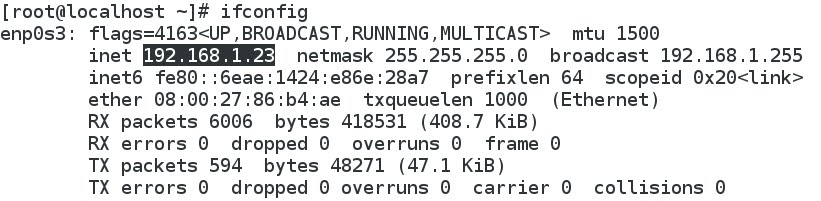
a) Kali Linux 192.168.1.27:
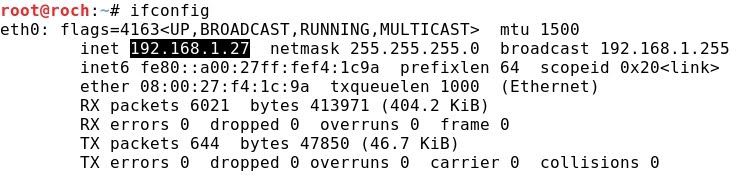
b) Ubuntu Linux 192.168.1.22:
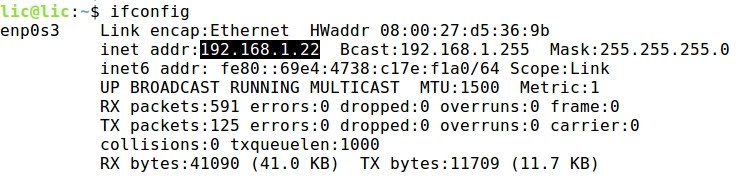
c) CentOS Linux 192.168.1.23:
- From Kali let's check that Ubuntu is running an SSH service:
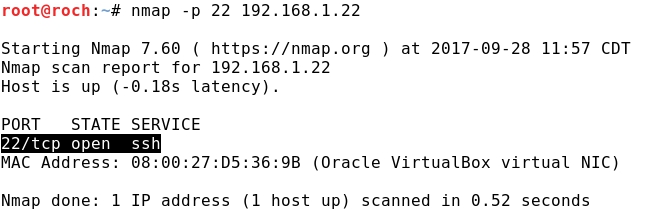
- From Kali let's check that CentOS is running an HTTP service:
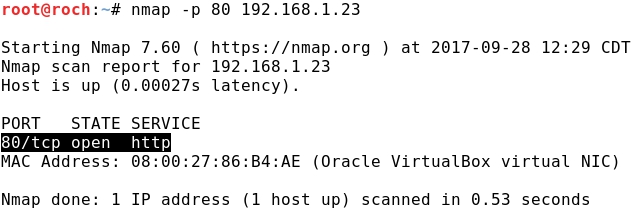
2 - SSH Tunneling with LOCAL port forwarding
- Now, from Kali we establish a SSH tunnel from local port 8080 to the remote port 80 at CentOS (192.168.1.23) tunneling through the Ubuntu (192.168.1.22) device.
- The SSH tunnel connection is successful, as we can check once the Ubuntu's shell is achieved:
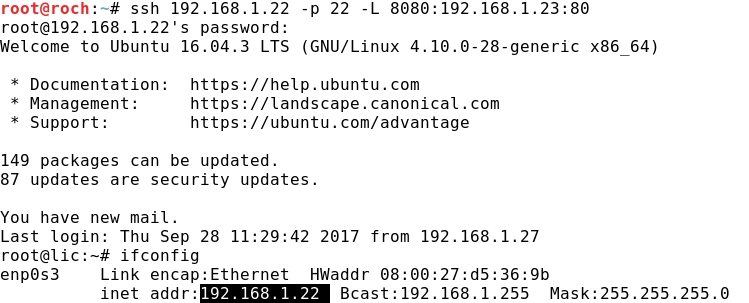
- Parameters used in previous command:
ssh <- protocol
192.168.1.22 -p 22 <- SSH server running on port 22
-L 8088 <- local port at Kali
192.168.1.23:80 <- HTTP server running on remote port 80
- Finally from Kali, browsing 127.0.0.1:8080 there is access to the remote web server at CentOS, so the final connection is also successful:
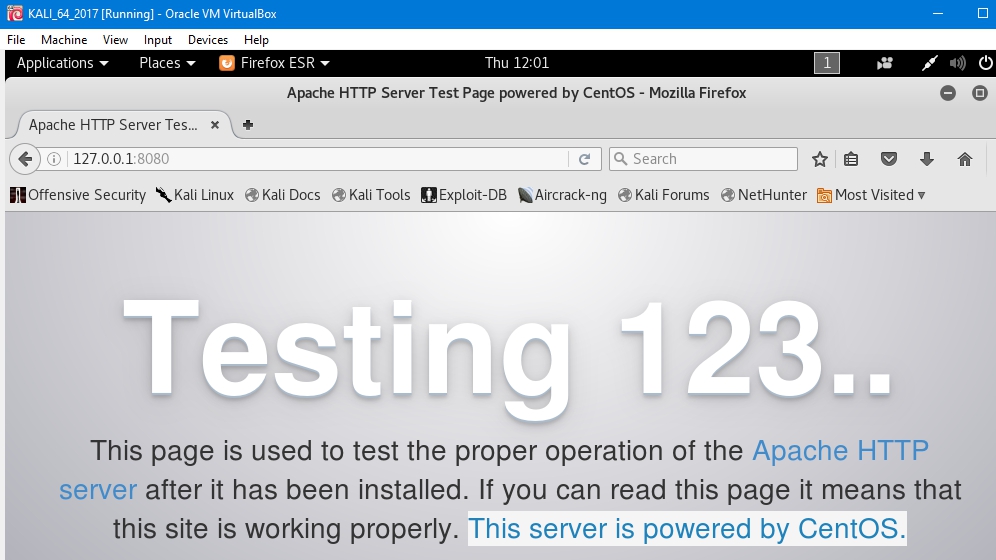
3 - Analyzing connections and corresponding ports with netstat
- It is important to notice that Kali only sees the SSH connection, not the HTTP one, regardless it is actually accessing the web server at CentOS. Using netstat:

- About Ubuntu it is also aware only of the SSH connection with Kali:

- Interestingly, the web server CentOS only recognizes an HTTP connection with Ubuntu ( not with Kali), and is totally unaware of the SSH tunnel from Kali, as the web access_log shows:
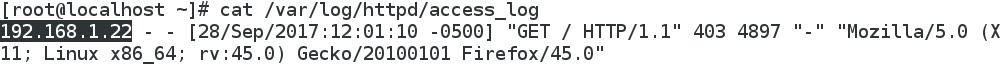
- The explanation of these results is that the local port 8080 at Kali redirects the traffic (encrypted with SSH cryptographic protocols) through the outbound SSH tunnel on port 22 to the remote web server.
ONLINE PASSWORD ATTACKS WITH MEDUSA, NCRACK AND HDYRA
- Layout for this exercise:

1 - Introduction
- Online password attacks involve password-guessing attempts for networked services that use a username and password authentication scheme.
- This includes services such as HTTP, SSH, VNC, FTP, SNMP, POP3, etc.
- In order to be able to automate a password attack against a given networked service, we must be able to generate authentication requests for the specific protocol in use by that service.
- Tools such as Medusa, Ncrack, Hydra and even Metasploit can be used for that purpose.
- The same wordlist will be used along this exercise:

2 - Medusa for HTTP brute force attack
- Medusa is a command line speedy, massively parallel, modular, login brute-forcer, supporting services which allow remote authentication.
- Medusa supports HTTP, FTP, CVS, AFP, IMAP, MS SQL, MYSQL, NCP, NNTP, POP3, PostgreSQL, pcAnywhere, rlogin, SMB, rsh, SMTP, SNMP, SSH, SVN, VNC, VmAuthd and Telnet.
- While cracking the password, host, username and password can be flexible input while performing the attack.
- Efficiency of the tool depends on network connectivity; for instance on a local system, it can test 2000 passwords per minute.
- With Medusa it is possible to perform a parallel attack, for instance cracking passwords of a few email accounts simultaneously, specifying the username list along with the password list.
- Installation and further information here:
http://foofus.net/goons/jmk/tools/
http://foofus.net/goons/jmk/medusa/medusa.html
- In the next example Medusa is used to perform a brute force attack against an htaccess protected web directory.
- First of all, let's check that the target has got open the port 80:

- Launching medusa (option -T 10 means 10 threads) against the target the attack is successful:

3 - Ncrack for RDP brute force attack
- Ncrack is a high-speed network authentication cracking tool built to help companies secure their networks by proactively testing all their hosts and networking devices for poor passwords.
- Ncrack was designed using a modular approach, a command-line syntax similar to Nmap and a dynamic engine that can adapt its behaviour based on network feedback. It allows for rapid, yet reliable large-scale auditing of multiple hosts.
- Protocols supported by Ncrack include RDP, SSH, HTTP(S), SMB, POP3(S), VNC, FTP, SIP, Redis, PostgreSQL, MySQL, and Telnet.
- Ncrack is available for many different platforms, including Linux, *BSD, Windows and Mac OS X. There are already installers for Windows and Mac OS X and a universal source code tarball that can be compiled on every system.
- For download and further information:
https://nmap.org/ncrack/
- In the next example ncrack is used against the Remote Desktop Protocol working at port 3389:
 - The attack is successful:
- The attack is successful:

4 - Hydra for SSH brute force attack
- Hydra is a fast network logon password cracking tool.
- It is available for Windows, Linux, Free BSD, Solaris and OS X, supporting many various network protocols like Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP, Rexec, Rlogin, Rsh, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP, SOCKS5, SSH (v1 and v2), Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
- Download Hydra here:
https://www.thc.org/thc-hydra/
- In the next example SSH credentials are attacked with Hydra.
- Checking that the SSH service is running at port 22 of the target:

- The attack is successful:
 5 - Hydra for FTP brute force attack
5 - Hydra for FTP brute force attack
- This attack is similar to the previous one, with the only difference that the attacked service is FTP working at port 21:

- The attack is successful:

EXTRACTING WINDOWS PASSWORD HASHES WITH PWDUMP/FGDUMP AND WCE (WINDOWS CREDENTIAL EDITOR)
- Layout for this exercise:

1 - Windows SAM, LM, NTLM and SYSKEY
- The Security Account Manager (SAM) is a database file in Windows XP, Windows Vista, and Windows 7 that stores users' passwords and it can be used to authenticate local and remote users.
- SAM uses hashing cryptographic measures to prevent unauthenticated users accessing the system.
- The user passwords are stored in a hashed format in a registry hive either as a LM or NTLM hash.
- This file can be found in %SystemRoot%/system32/config/SAM and is mounted on HKLM/SAM.
https://en.wikipedia.org/wiki/Security_Account_Manager
- LAN MAnager (LM) hash is a compromised password hashing function that was the primary hash that Microsoft LAN Manager and Microsoft Windows versions prior to Windows NT used to store user passwords.
- Support for the legacy LM protocol continued in later versions of Windows for backward compatibility, but was recommended by Microsoft to be turned off by administrators. As of Windows Vista, the protocol is disabled by default.
- LM authentication uses a particularly weak method of hashing a user's password that makes such hash crackable in a matter of seconds using rainbow tables, or in few hours using brute force.
- Weakness of LM hashes lies in their implementation; since they change only when a user changes their password, they can be used to carry out a Pass The Hash Attack (PTH).
https://en.wikipedia.org/wiki/LAN_Manager
- The NT LAN Manager (NTLM) is a suite of Microsoft security protocols that provides authentication, integrity, and confidentiality to users.
- NTLM is the successor to the LM authentication protocol.
- NTLM remains vulnerable to the Pass The Hash (PTH) attack, which is a variant on the reflection attack. For example, Metasploit can be used in many cases to obtain credentials from one machine which can be used to gain control of another machine.
- The Squirtle toolkit can be used to leverage web site cross-site scripting attacks into attacks on nearby assets via NTLM.
- Amplia Security discovered several flaws in the Windows implementation of the NTLM authentication mechanism which broke the security of the protocol allowing attackers to gain read/write access to files and remote code execution.
https://en.wikipedia.org/wiki/NT_LAN_Manager
- In an attempt to improve the security of the SAM database against offline software cracking, Microsoft introduced the Syskey function in Windows NT 4.0.
- Syskey is a utility that encrypts the hashed password information in a SAM database in a Windows system using a 128-bit RC4 encryption key that, by default, is stored in the Windows registry.
- Syskey can optionally be configured to require the user to enter the key at boot time as a startup password or load it on removable storage media (e.g., USB flash drive).
- It was meant to protect against offline password cracking attacks by preventing the possessor of an unauthorised copy of the SAM from extracting useful information from it.
- However, it is commonly being misused by scammers to lock victims out of their own computers in order to coerce them into paying a ransom.
https://en.wikipedia.org/wiki/Syskey
2 - pwdump/fgdump
- pwdump/fgdump are password hash dumpers for Windows 2000 and later systems.
- pwdump/fgdump are capable of dumping LM/NTLM hashes as well as password hash histories.
- pwdump/fgdump perform in-memory attacks by injecting a DLL containing the hash dumping into the Local Security Authority Subsystem (LSASS) process memory.
- The LSASS process has the necessary privileges to extract password hashes as well as many useful API that can be used by the hash dumping tools.
- fgdump is a more powerful version of pwdump, because pwdump tends to hang when antivirus is present, so fgdump takes care of that by shutting down and later restarting a number of AV programs.
- fgdump was born out of frustration with current antivirus (AV) vendors who only partially handled execution of programs like pwdump, some of them would sometimes allow pwdump to run, sometimes not, and sometimes lock up the box.
- For further information and downloading pwdump/fgdump:
http://foofus.net/goons/fizzgig/fgdump/downloads.htm
https://www.darknet.org.uk/2006/10/download-pwdump-142-and-fgdump-134-windows-password-dumping/
- fgdump.exe is run from the Windows command line with administrator privileges:

- Running fgdump.exe:

- Reading the file 127.0.0.1.pwdump the NTLM hashes for all users are displayed:

3 - Windows Editor Credentials (WCE)
- Windows Credentials Editor (WCE) is a post-exploitation security tool that allows to list logon sessions and add, change, list and delete associated credentials (ex.: LM/NT hashes, plaintext passwords and Kerberos tickets).
- WCE can be used, for example, to perform pass-the-hash on Windows, obtain NT/LM hashes from memory (from interactive logons, services, remote desktop connections, etc.), obtain Kerberos tickets and reuse them in other Windows or Unix systems and dump cleartext passwords entered by users at logon.
- WCE is a security tool widely used by security professionals to assess the security of Windows networks via Penetration Testing. It supports Windows XP, 2003, Vista, 7, 2008 and Windows 8.
- WCE works by using DLL injection or by directly reading the Local Security Authority Subsystem (LSASS) process memory. This second method is more secure in terms of operating system stability, because code is not injected into a highly privileged process.
- For further information and downloading WCE:
http://www.ampliasecurity.com/research.html
- VCE is run from the Windows command line with administrator privileges:

- The output of running wce.exe displays both the LM and NTLM hashes of the passwords from all users currently logged on:






















































