2.10
- WiFishing: creation of multiple honeypots
- The
creation of just 1 fake Access Point or honeypot is not always
enough, because the victim would connect automatically to only one AP
matching the stored network configuration. How the attacker would
force the client to connect to its own fake AP, and not other one
available, without knowing a priori the preferred type of encryption
of the victim?
- For
that reason, and for the purpose of penetration testing, it is very
handy to create several fake APs with the same SSID, but each of one
matching diferent types of encryption methods: for instance Open,
WEP, WPA-PSK and WPA2-PSK, with TKIP or AES-CCMP.
- So,
taking 4 different encryption options, it would be necessary to
create 4 virtual interfaces: mon0, mon1, mon2 and mon3, using
airmon-ng start wlan0 repeatedly at the attacker "kali"
machine.
- mon0:
- mon1:
- mon2:
- mon3:
- Now,
there are 4 virtual interfaces working in monitor mode:
- The
command airbase-ng holds interesting options to fake APs:
- For
creating WEP, option -W 1 is available:
- For
creating WPA option -z is used, being 2 for TKIP and 4 for AES-CCMP.
Same for WPA2 using -Z:
- The
first honeypot called "puntodeacceso" doesn't have any
encryption, it is Open, so no option is used. MAC address will be
AA:AA:AA:AA:AA:AA, working in mon0 monitor interface:

- The
second honeypot is also called "puntodeacceso" and uses WEP
encryption (-W 1). MAC address will be BB:BB:BB:BB:BB:BB, working in
mon1 monitor interface:
- The
third honeypot is also called "puntodeacceso" and uses
WPA-PSK TKIP encryption (-z 2). MAC address will be
CC:CC:CC:CC:CC:CC, working in mon2 monitor interface:
- The
fourth honeypot is also called "puntodeacceso" and uses
WPA2-PSK TKIP encryption (-Z 2). MAC address will be
DD:DD:DD:DD:DD:DD, working in mon3 monitor interface:
- It
can be verified the existence of the 4 honeypots, all sharing the
same ESSID, each one with different type of encryptions and different
number of MAC addresses:
- The
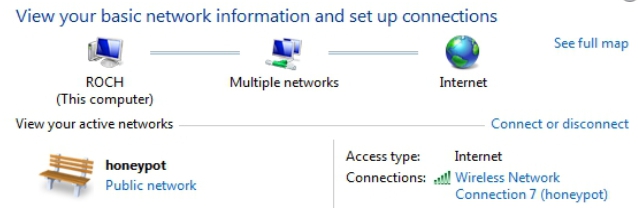
question that arises now is: Which one would the victim "roch"
pick up to connect to?
- Based
on the Preferred Network List, in this case the client "roch"
has got a stored network called "puntodeacceso":
- Also,
the configuration forces to connect automattically to the network
"punto de acceso"when it is in range:
- The
stored security configuration uses WPA with TKIP encryption:
- So,
no doubt that the picked up honeypot to be connected by the victim
"roch" (whose MAC adress is 28:C6:8E:63:15:6B) will be the
third honeypot, which uses WPA-TKIP and has got CC:CC:CC:CC:CC:CC as
MAC address, because it is the only one that matches the stored
configuration:
- This
practice has shown how to create the appropiate bait for a victim,
offering fake APS or honeypots with different encryptions modes,
assuming that one of them would match the stored security
configuration mode by the victim.