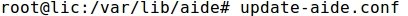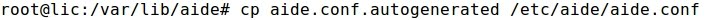SYMMETRIC CRYPTOGRAPHY WITH GPG2 AND AES ALGORITHM
- Layout for this exercise:

1 - Introduction
- Symmetric key algorithms use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. The symmetric key is a shared secret between two or more parties that can be used to maintain a private information link.
https://en.wikipedia.org/wiki/Symmetric-key_algorithm
- The Advanced Encryption Standard (AES), also known by its original name Rijndael, is a specification for the encryption of electronic data and adopted by the U.S. government and now used worldwide. The algorithm described by AES is a symmetric-key algorithm, meaning the same key is used for both encrypting and decrypting the data.
https://es.wikipedia.org/wiki/Advanced_Encryption_Standard
- gpg2 is the OpenPGP part of the GNU Privacy Guard (GnuPG). It is a tool to provide digital encryption and signing services using the OpenPGP standard:
https://en.wikipedia.org/wiki/GNU_Privacy_Guard


2 - Encrypting and decrypting (locally) a text file
- The goal of this exercise is to implement a symmetric cryptography example uusing the gpg2 Linux command and the AES algorithm.

- Creating a text file and writing some plaintext:



- Encrypting the text file with the symmetric algorithm AES of 256 bits, a passphrase is required to be entered and reentered:



- As a consequence a new encrypted message is created with the extension .gpg:

- The content of message.txt.gpg is encrypted and the chipertext unreadable:

- Decrypting the file message.txt.gpg the passphrase is required:


- Let's confirm that the decryption has been successful because decrypted_message.txt and the original message.txt match their contents of the plaintext file:

3 - Decrypting a text file (remotely)
- Now, let's repeat the process implementing a potential real example where a remote user receives an encrypted message and decrypts it (using a previously shared key with the sender).
- The sender (user lic at Ubuntu) uses the secure file transfer protocol SFTP to send the ciphertext or encrypted file message.txt.gpg:


- The receiver (user marie at Debian) successfully receives the encrypted message:

- As expected, the content of the encrypted file is unreadable:

- Decrypting, the remote user or receiver marie is invited to enter the same passphrase than the sender lic:


- Once the passphrase is entered, the receiver can read the plaintext:

- It is important to distinguish two concepts. On the one hand, the original plain text has been encrypted with the symmetric algorithm AES. On the other hand, the encrypted file has been sent over the network with SFTP. However, there are two levels of different encryption, while the first level refers to the content of the text file, the second level refers to the transport, communication or transfer of the file.