PORT REDIRECTION WITH RINETD TO HTTP SERVER AND REMOTE DESKTOP PROTOCOL SERVERS
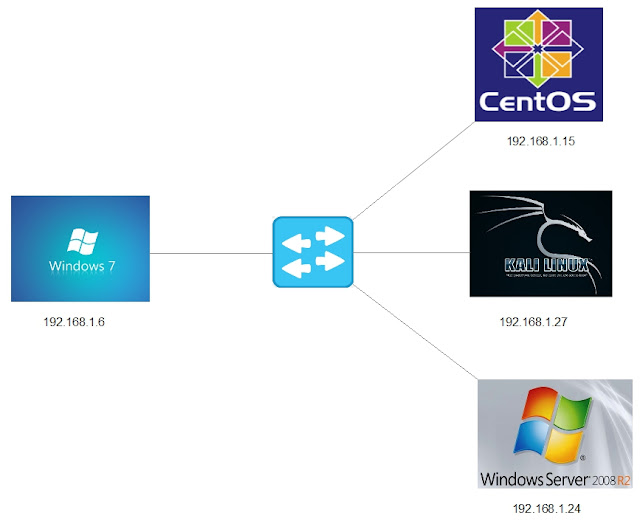
- Layout for this exercise:
1 - Introduction
- rinetd redirects connections from one IP address and port to another with basic IP based access control.
- rinetd is a single process server which handles any number of connections to the address/port pairs specified in the file /etc/rinetd.conf.
- Since rinetd runs as a single process using nonblocking I/O, it is able to redirect a large number of connections without a severe impact on the machine.
- This makes it practical to run services on machines inside an IP masquerading firewall.
2 - Port redirection to HTTP server
- Installing the service rinetd at the Kali Linux machine:
- Editing /etc/rinetd.conf:
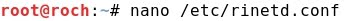

- The configuration parameters are:
bindadress = 192.168.1.27 (Kali Linux)
bindport = 3333 (redirected port at Kali Linux)
connectaddress = 192.168.1.15 (CentOS where the HTTP server is enabled)
connectport = 80 (HTTP port at CentOS)
- Restarting the service rinetd:

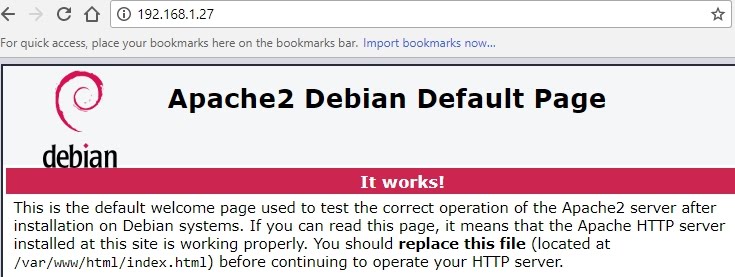
- Now, connecting from Windows 7 normally to 192.168.1.27 (port 80) the Apache Server home page at Kali Linux is displayed:
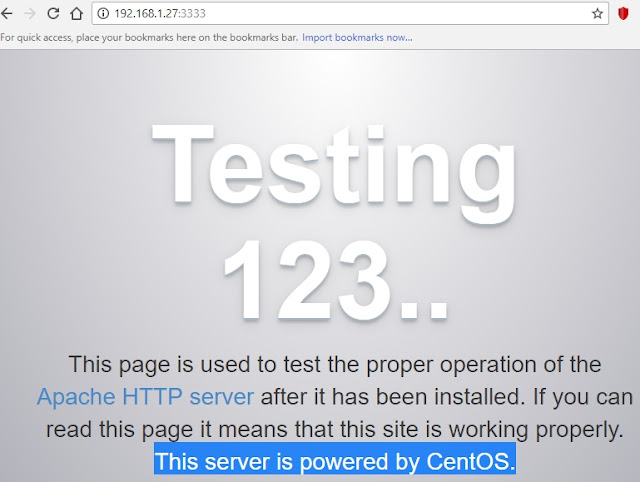
- However, when connecting from Windows 7 to port 3333 (192.168.1.27:3333) there is a redirection to the Apache Server located at CentOS Linux machine:
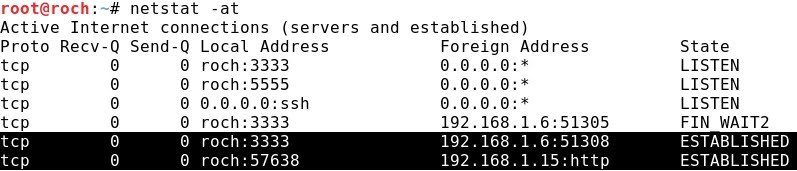
- Running netstat at Kali Linux, the redirected connection from Kali Linux local port 3333 to remote CentOS port 80 is displayed:
- It is interesting to notice that the CentOS Linux HTTP server does not have any news from its "hidden client" Windows 7 (192.168.1.6), because the only "connection" to its port 80 detected by netstat is the one coming from the proxy Kali Linux (192.168.1.27):
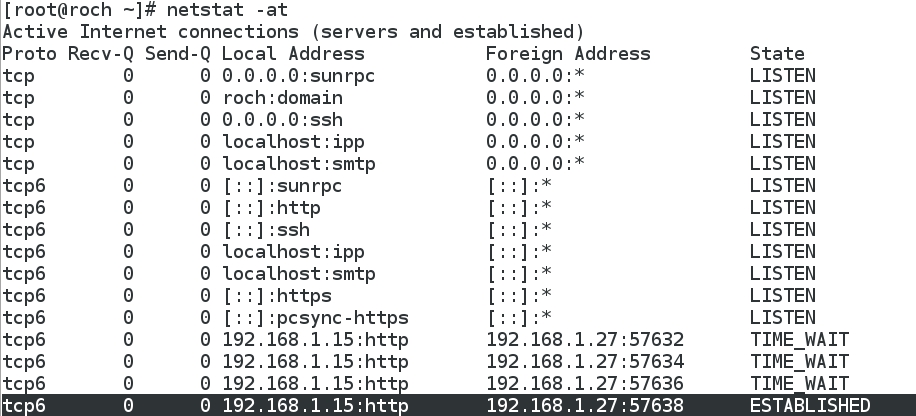
3 - Port redirection to Remote Desktop Protocol server
- Editing again /etc/rinetd.conf:
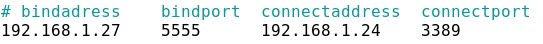
- The configuration parameters are:
bindadress = 192.168.1.27 (Kali Linux)
bindport = 5555 (redirected port at Kali Linux)
connectaddress = 192.168.1.24 (Windows Server 2008 where RDP server is enabled)
connectport = 3389 (RDP port at Windows Server 2008)
- Restarting the service rinetd:

- Connecting from Windows 7 with RDP to Kali Linux trough port 5555:
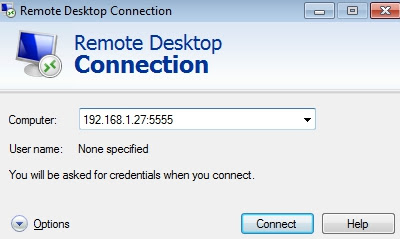
- Authenticating:
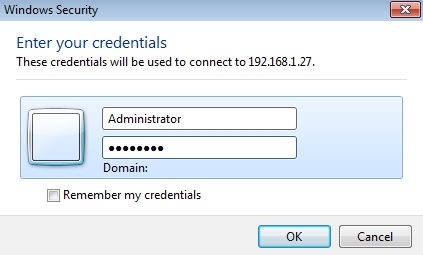
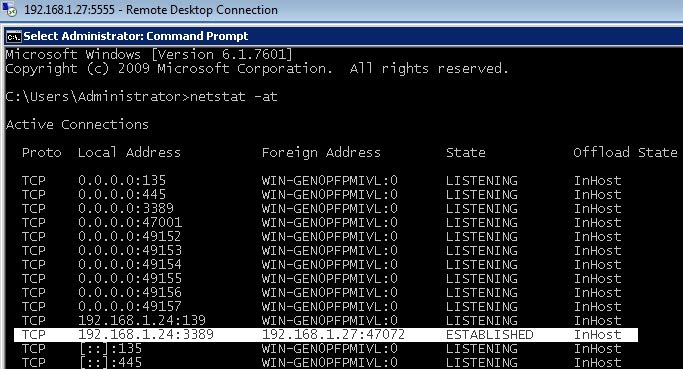
- The RDP connection to 192.168.1.24 (Windows 2008) is successful, but let's notice that the connection is being redirected trough 192.168.1.27:5555 (Kali Linux Machine):
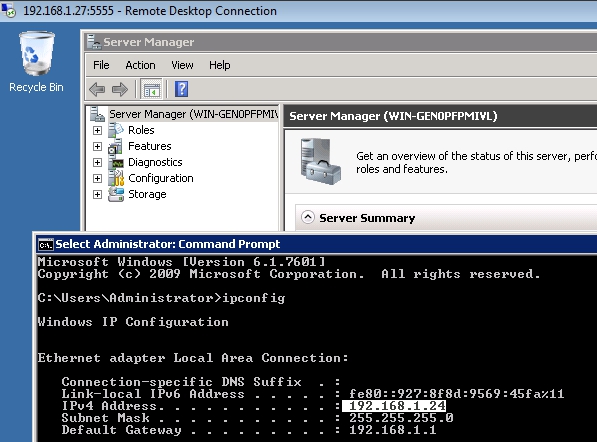
- Running netstat at Kali Linux, the redirected connection from local port 5555 to remote port 3389 is displayed:
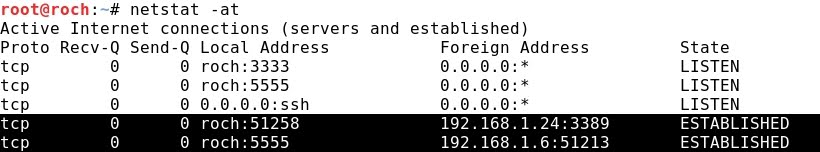
- Interestingly, running netstat shows that Windows 2008 is totally unware of the "hidden client" Windows 7 (192.168.1.6) that originated and actually is taken advantage of the RDP connection. In other words, the only connection detected by Windows 2008 is from the proxy Kali Linux (192.168.1.27):