COUNTING NETWORK TRAFFIC GENERATED BY NMAP OPTIONS
- Layout for this exercise:

1 - Introduction
- The goal of this exercise is to compare traffic sent by different NMAP options while scanning ports of a target.
- For that purpose the bash script TrafficCounter.sh uses Linux Iptables to measure incoming and outgoing traffic to the target 192.168.1.7.
- Every time the Nmap is used the script is run in order to clean the current status of the Iptables firewall, with options -Z (zero counters in all chains) and -F (deletes all rules in all chains).


- Giving execution permissions to the script:

- After Nmap has been run Iptables shows the traffic sent to the target, with options -vn ( verbose and numeric output) and -L (lists the rules):

2 - Nmap -sT
- nmap -sT establishes a full TCP handshake connection:


- The traffic originated is big, 122 Kbytes:

3 - Nmap -sS
- nmap -sS scan does not establish a full TCP handshake, just half connection:


- The traffic generated is 88 Kbytes:

4 - Nmap -sV
- nmap -sV detects versions of the the services running at the ports:


- Traffic generated is 98 Kbytes:

5 - Nmap -O
- nmap -O discovers the Operating System of the target:


- The traffic generated is 95 Kbytes:

6 - Nmap -sU
- nmap -sU scans UDP ports:


- Traffic generated is less than previous cases, 58 Kbytes:

7 - Nmap -sn
- nmap -sn discovers up/down targets of a given subnet:

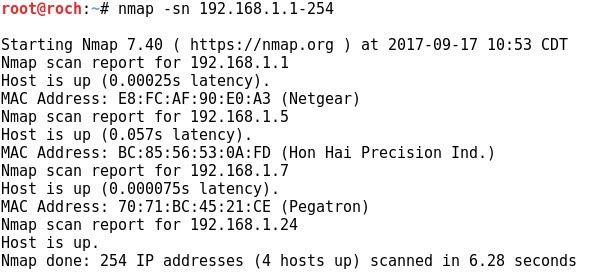
- The traffic generated is almost nothing:

8 - Nmap -sP
- nmap -sP discovers whether the target is up/down:


- The traffic generated is negligible:

9 - Nmap -sT all ports
- nmap -sT -p 1-65535 scans all ports of the target:


- The traffic generated is huge, 7878 Kbytes:

10 - Nmap --top-ports
- nmap --to-ports scans only the most important or usual ports, up to a specified amount of them, in this case 10:


- The generated traffic is small, 852 bytes:
