COMMAND INJECTION WITH BURP FOR NETGAR ROUTER EMULATED FIRMWARE
- Layout for this exercise:

1 - Introduction
- This exercise is based on the Command Injection attack for NetGear devices registered here:
http://firmware.re/vulns/acsa-2015-001.php

- The vulnerability affects a great range of NetGear products, including the router WNAP320:

- One of the affected scripts is called boardDataWW.php, that will be analyzed for the purpose of attacking it through a Command Injection, sending a crafted input taking advantage of the lack of sanitization:

- The vulnerable section of the script uses an insecure call to PHP function exec(), accepting any type of input for the parameter 'macAddress':

2 - Setting up the lab
- Unzipping and decompressing the firmware of the NetGear router:


- Extracting the .squashfs file:

- A new folder is extracted:

- Inside, we can find the whole root file system of the firmware, ready to be analyzed:


3 - Analyzing the vulnerable PHP script
- First, let's try to locate the vulnerable script boardDataWW.php, using the command locate:


- Opening boardDataWW.php we find the call to the PHP function exec():


- The parameter 'macAddress' is passed without further sanitization about the standard MAC address format:

- Let's see how exec() works:

4 - Intercepting with Burp
- Once the firmware emulated is available (as done in previous exercise):

- Going to the affected script:

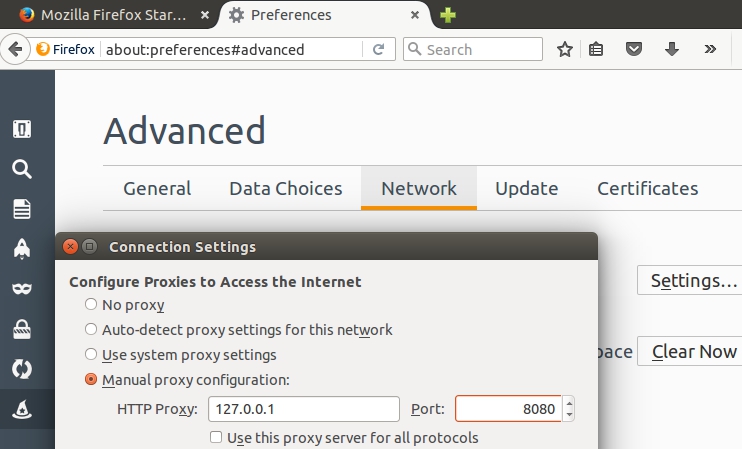
- Enabling the proxy at the browser:

- Launching Burp:



- Enabling Burp to intercept Client requests and Server responses:

- Sending a fake MAC address:

- The message is intercepted:

5 - Launching the attack
- Sending the request to the Repeater:


- Now, let's try to craft the MAC address input so that the content of /etc/passwd is leaked to a file located into the root of the web page:
cp /etc/passwd /home/www/passwd # from here it is a comment

- Clicking Go and trying to access passwd from the browser:

- The file passwd is open and saved:

- The content of /etc/passwd has been leaked, so the attack is successful:

- Also, because Burp has been enabled to intercept the Server responses, the whole content is displayed:

- It is interesting to notice that this attack has been launched against an "emulated firmware", and not against an actual physical device.